What Is the HIPAA Security Rule?
April 22, 2021 by Richard Bailey ( 173 ) under HIPAA Compliant Hosting
0 Comments
The Healthcare Insurance Portability and Accountability Act (HIPAA) was enacted into law by President Bill Clinton on August 21st, 1996. In a landmark achievement, the government set out specific legislation designed to change the US Healthcare System now and forever. The rules handed control back to the patient over how their personal information is processed and maintained, while also encouraging healthcare institutions to embrace and migrate to digital technology.
 Why is the HIPAA Security Rule Important?
Why is the HIPAA Security Rule Important?
Two main objectives of the new legislation were to enable Americans to keep their existing health insurance when moving between jobs and introduce enforceable privacy controls over protected health information (PHI).
- The first objective – to enable Americans to move their health insurance between jobs – was a clear-cut goal that was achieved almost overnight. This is how the first P in HIPAA – “Portability” – became effective. This aspect of the law is rarely discussed, simply because the goal was achieved immediately.
- The second objective of the law, to enforce privacy over health information, is what most healthcare organizations and professionals are primarily concerned with: the “Accountability” portion of HIPAA. This objective was created to maintain the privacy and security safeguards of US citizens’ PHI.
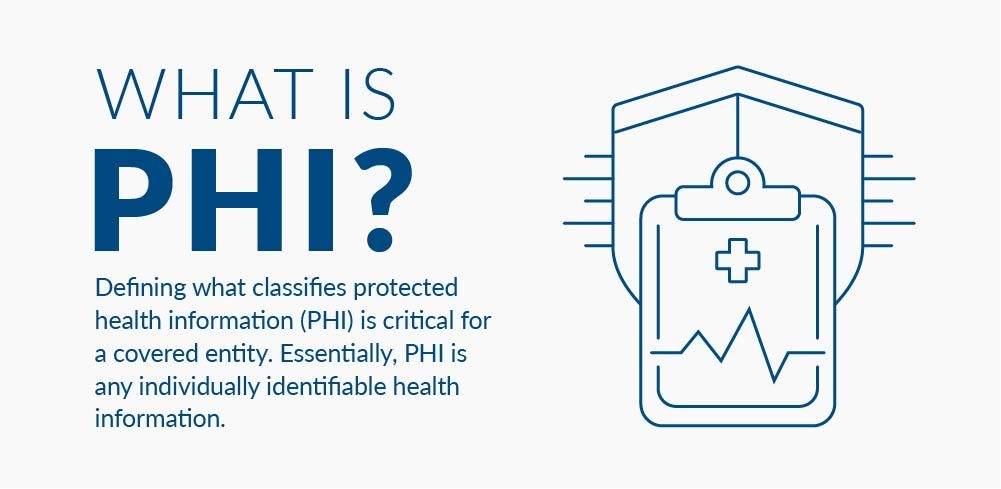
 What is PHI?
What is PHI?
Defining what classifies protected health information (PHI) is critical for a covered entity. Members of the public and healthcare professionals may have different viewpoints on what exactly constitutes PHI, but essentially, PHI is any individually identifiable health information.
You may also encounter the acronym ePHI or e-PHI, or electronic protected health information. Electronic protected health information is protected health information stored or accessed in an electronic format. Common examples include:
- Treatment reports
- Test results
- Prescription information
- Any information that includes the name
- Phone numbers
- Addresses
- Social security numbers
- Medical records numbers
- Health insurance details
- …and so on
 What is a Covered Entity?
What is a Covered Entity?
Covered Entities (CE) are organizations that handle PHI or e-PHI during day-to-day business operations. A Covered Entity must abide by HIPAA regulations, which are enforced by the HSS.
The U.S. Department of Health and Human Services (HHS) officially defines a Covered Entity as belonging to one of the following groups:
- Healthcare Providers – such as doctors, dentists, nursing homes, pharmacies, etc.
- Health Plans – health insurance companies, HMOs, Medicare, Medicaid, etc.
- Clearinghouses – transcription services, etc.
What is a Covered Entity that handles PHI and ePHI?
What is a Business Associate?
Business Associates are organizations that work with Covered Entities in handling e-PHI or PHI. Just as a Covered Entity must abide by HIPAA regulations in handling e-PHI or PHI, so too must any Business Associate they work with. Atlantic.Net is a Business Associate of each healthcare organization with whom we process, store, manage or otherwise deal with electronic protected health information.

Therefore, we are legally obliged to sign a contract of service with each organization to guarantee our HIPAA compliance status. We outline our security policies and procedures and our administrative, physical, and technical safeguards that detail how we maintain the confidentiality, integrity, and availability of electronic protected health information.
 How are HIPAA security rules and privacy rules different?
How are HIPAA security rules and privacy rules different?
In April 2003, Title II of HIPAA directed the US Department of Health and Human Services (HHS) to develop a series of guidelines and standards to safeguard patient health data. To make these guidelines and standards clear and effective, the HHS developed two additional decrees known as the Privacy Rule and the Security Rule.
The official title of the Privacy Rule is the “Standards for Privacy of Individually Identifiable Health Information.” As we stated at the beginning of this article, our main focus will be the Security Rule. However, it is worth noting that per the official title of the Privacy Rule, for purposes of enforcement of the Security Rule, the patient health data must be traceable to a specific person to require protection.
It can be confusing to differentiate between these standards, mainly because the regulations sound quite similar. Isn’t security a way to maintain privacy, after all? That actually is a correct understanding of HIPAA security compliance: according to the HHS’s own description, the HIPAA Security Rule “operationalizes the protections contained in the Privacy Rule by addressing the technical and non-technical safeguards that organizations called ‘a covered entity’ must put in place to secure individuals electronically protected health information (ePHI).”
So, in actuality, the Security Rule is designed to complement the Privacy Rule in its entirety.
 What is the Security Rule of HIPAA?
What is the Security Rule of HIPAA?
The full title of the HIPAA Security Rule decree is “Security Standards for the Protection of Electronic Protected Health Information,” and as the official title suggests, the Security Rule is a ruling that defines the exact stipulations required to safeguard ePHI, specifically relating to how the information is stored and transmitted between digital devices.
 What is the Privacy Rule of HIPAA?
What is the Privacy Rule of HIPAA?
Its full name is the “Standards for Privacy of Individually Identifiable Health Information.” As we stated at the beginning of this article, our main focus is the Security Rule. This rule defines that patient health data must be traceable to a specific person to fall under the scope of HIPAA’s requirements. That specific wording allows anyone who wants to study health and medical trends the legal wiggle room to do so by omitting personally identifiable information before transmission.
 Who does the HIPAA security rule apply to?
Who does the HIPAA security rule apply to?
HIPAA regulations mean that the Security Rule requires anyone that processes or handles PHI, including ePHI, to follow its mandate. This can be any medical institution, third-party couriers, dedicated hosting or cloud hosting providers, or clearinghouses. If you process data that contains PHI, then the HIPAA Security Rule Applies!
 When does the HIPAA Security Rule Not apply?
When does the HIPAA Security Rule Not apply?
If the PHI process uses redacted or encapsulated information, the data much be completely untraceable to the owner. If you are in doubt, consult your legal advisors.
 What are the three standards of the HIPAA Security Rule?
What are the three standards of the HIPAA Security Rule?
The Security Rule outlines three standards by which to implement policies and procedures. These safeguards create a blueprint for security policies to protect health information.
The 3 safeguards are:
- Physical Safeguards for PHI
- Technical Safeguards for PHI
- Administrative Safeguards for PHI
 What are the Physical Safeguards for electronic Protected Health Information (ePHI)?
What are the Physical Safeguards for electronic Protected Health Information (ePHI)?
The physical safeguards refer to the implementation specifications for real-life physical controls on digital devices that store and handle e-PHI.
Some of the key areas for consideration are:
- How old or faulty equipment is replaced – for example, how ePHI media is destroyed
- What personnel access levels are granted to in-scope systems containing ePHI; specifically, covered entities must ensure that access is only granted to employees with a relevant level of authorization
- How to train 3rd-party IT professionals when accessing the in-scope equipment for repairs
 What are the Technical Safeguards for Protected Health Information?
What are the Technical Safeguards for Protected Health Information?
The technical safeguards of the Security Rule are more easily defined and include the technical aspects of any networked computers or devices that communicate with each other and contain PHI in their transmissions.
These safeguards include enhanced network security, perimeter firewalls, cybersecurity authentication protocols, and more. Any security measures that can be implemented on system software or hardware belonging to the HIPAA security rule technical safeguards category.
 What are the Administrative Safeguards for Protected Health Information?
What are the Administrative Safeguards for Protected Health Information?
The final standard, administrative safeguards, covers how covered entities must set up their employee policies and procedures to comply with the Security Rule. Think of it as a separate, dedicated portion of employee training, both for management and labor defining who gets access and what they can and cannot do once access is granted.
 How do I comply with the HIPAA Security Rule?
How do I comply with the HIPAA Security Rule?
Working your way through federal legislation, as with many laws and bills, can be an exceedingly lengthy, intricately complex, and almost aggressively dense process. Trying to sit down and read through the entire Health Insurance Portability and Accountability Act front to back would no doubt prove to be a significantly challenging process, difficult not only to read in its entirety but also to absorb and understand.
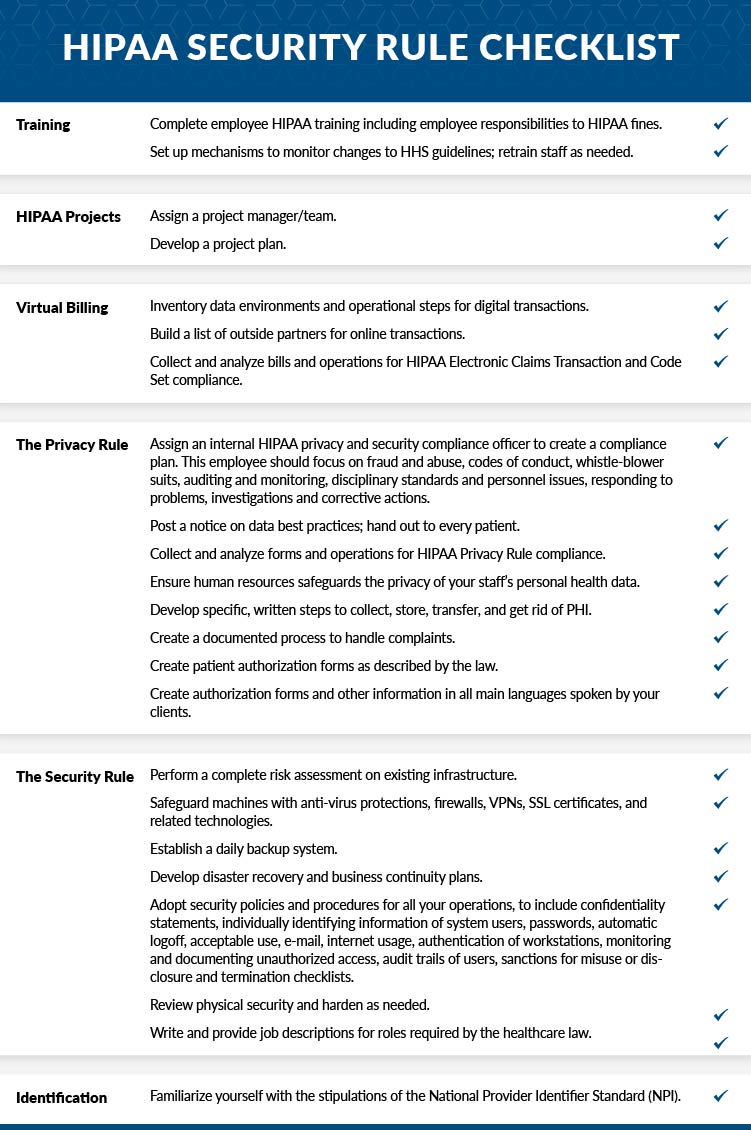
We have prepared a checklist to help you understand how to comply with the HIPAA Security Rule. Although this checklist should not be considered comprehensive, it will help to organize your position on the various safeguards.
Take the time to go over this HIPAA Security Rule Checklist in full and be sure to involve all parties with knowledge of each area before checking off the boxes.
 When HIPAA data is transmitted electronically, how is it encrypted?
When HIPAA data is transmitted electronically, how is it encrypted?
VPN traffic must be encrypted to comply with HIPAA technical safeguards, and it doesn’t matter if a remote access point or site-to-site VPN is used.
Take telehealth, for example. Sensitive voice and video may be shared, end-to-end encryption will protect the integrity of the connection, making it all but impossible to crack. Not only would an attacker have to break the encryption, but they would also have to perform a man-in-the-middle attack.
The VPN creates a secured network tunnel where the end user can safely transmit sensitive data without the risk of any data being compromised. With today’s rapid internet speeds, there is no noticeable difference in the user experience on a VPN connection compared with accessing the infrastructure directly outside of latency depending on physical distance from the data center. The possibility of latency issues caused by the distance between the end-user and the data center is why Atlantic.Net has so many different physical locations across the globe.
 Is it true that when PHI is encrypted, it is no longer regulated under HIPAA?
Is it true that when PHI is encrypted, it is no longer regulated under HIPAA?
Absolutely not. Protected health information (PHI) is regulated by the laws of HIPAA legislation no matter what the encryption status of the data is. It is not mandatory to encrypt PHI at rest, but it is highly advisable.
 When was the HIPAA security rule enacted?
When was the HIPAA security rule enacted?
The Health Insurance Portability and Accountability Act (HIPAA) was enacted on August 21, 1996, when it was signed into law by President Bill Clinton. However, there have been subsequent major updates to the legislation, most significantly the addition of the HIPAA Privacy Rule and Security Rule.
Proposed on November 3, 1999, the HIPAA Privacy Rule was enacted on December 20, 2000. This rule sought to define PHI and regulate its use and disclosure. The HIPAA Security Rule was proposed in 1998, with compliance coming into effect on April 21, 2005. The HIPAA Security Rule was put into place to protect the integrity and availability of electronic PHI.
In 2009, further amendments included the introduction of the Health Information Technology for Economic and Clinical Health Act (HITECH) and the Breach Notification Rule.
 Is encryption mandatory for HIPAA?
Is encryption mandatory for HIPAA?
File data encryption is not a mandatory law for HIPAA-Compliance (yet); however, it is strongly advised that all files should be encrypted at rest with at least an AES256 bit encryption cipher. You will need a very good reason when audited as to why the files are not encrypted, and a roadmap of creating encryption is expected as part of a risk assessment.
VPN encryption is a mandatory requirement. HIPAA recommends using end-to-end encryption (E2EE); this standard means that only the sender and receiver can view or access the data (it is encrypted everywhere but at the endpoints). Data is not stored on an intermediate server, such as a content server, during the data transfer, making the entire data transaction incredibly secure.
You should also consider making your email platform encrypted, encrypting user laptops, mobile phones, tablets, and strictly managing your employee’s BYOD habits. Backups must be encrypted, as well as any in-scope database.
Need help with encryption? Get in touch today!
 Why is encryption is important in HIPAA?
Why is encryption is important in HIPAA?
Data encryption is a method of translating data into a protected format that can only be read by the person or computer with the decryption key. Unencrypted data, sometimes called plaintext, is readable by humans and computers. Encrypted data, sometimes called ciphertext, is only readable by the holder of the secret (encryption) key.
It is highly recommended to encrypt all PHI data, and the only way to achieve this standard is to use AES-256 encryption for PHI data stored at rest and in transit. By default, Atlantic.Net encrypts all data. Surprisingly, holding PHI data encrypted at rest is not mandatory, but you need to have a very good excuse when you are audited as to why you are not encrypting data at rest. Only encrypting PHI in transit is mandatory.
 Is AES 256 HIPAA Compliant?
Is AES 256 HIPAA Compliant?
Yes, the AES256 encryption standard is compliant with HIPAA standards. It is advisable to encrypt with the strongest encryption ciphers. RSA encryption is also HIPAA compliant and is considered much stronger, as up to 4096bit RSA encryption is possible.
HIPAA Security Rule Checklist
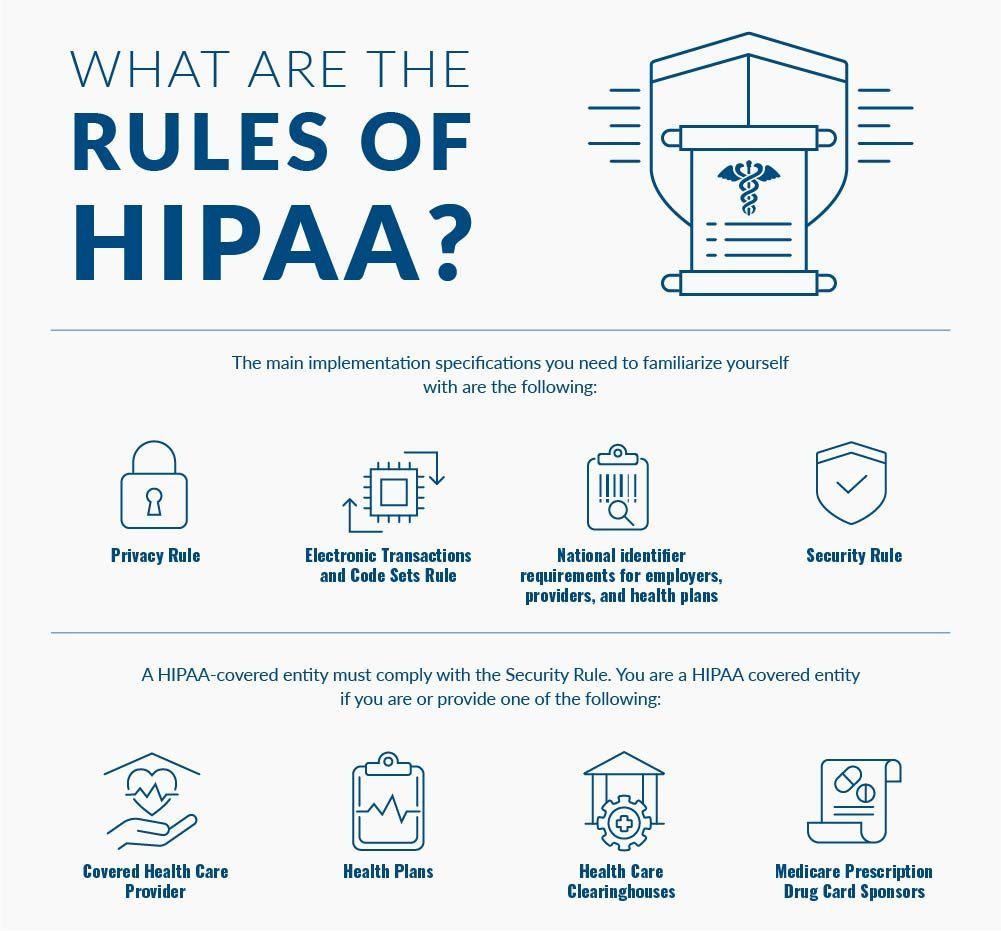
 What are the rules of HIPAA?
What are the rules of HIPAA?
The main implementation specifications you need to familiarize yourself with are the following:
- Privacy Rule
- Electronic Transactions and Code Sets Rule
- National identifier requirements for employers, providers, and health plans
- Security Rule
The tricky bit is that not all the above standards are relevant to all entities.
A HIPAA-covered entity must comply with the Security Rule. You are a HIPAA-covered entity if you are or provide one of the following:
- Covered Health Care Provider
- Health Plans
- Health Care Clearinghouses
- Medicare Prescription Drug Card Sponsors
To ensure you’re complying with the Security Rule, take this step-by-step approach:
Assess your current security, taking special note of any risks and gaps (this is called a risk assessment or risk analysis, and some organizations specialize in hosting-related needs ensures that you can spend your time and energy worrying about other aspects of HIPAA compliance, and leaving the Technical and Physical safeguards for HIPAA and security (listed above) to us. Get in touch with us today and find out how our team of HIPAA-compliant hosting specialists can make your life easier with any of our Cloud Hosting Solutions.
 How Can I Audit my Network for HIPAA Compliance?
How Can I Audit my Network for HIPAA Compliance?
This is a tough assignment even for professionals, and it is one of the principal reasons customers outsource to a HIPAA-compliant hosting provider like Atlantic.Net. Our engineers have vast networking experience looking for vulnerabilities at the network layer.
HIPAA best practices demand that a network is secured, segregated, and protected by a Managed Network Firewall. Traffic must be encrypted when it leaves the network, and the network must be audited by some form of Intrusion Protection System to monitor for unauthorized changes to protected health information.
Need help with your managed firewall? Get in touch today!
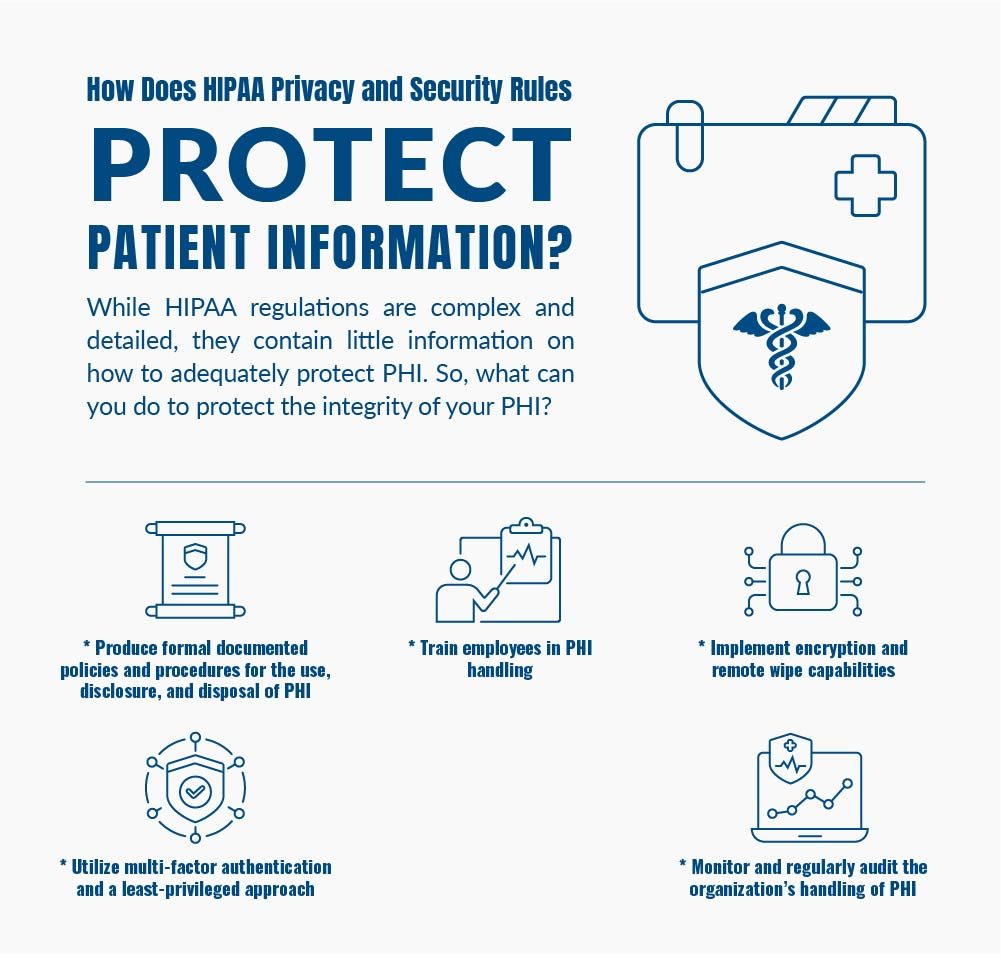
 How Do HIPAA Privacy and Security Rules Protect Patient Information?
How Do HIPAA Privacy and Security Rules Protect Patient Information?
While HIPAA regulations are complex and detailed, they contain little information on how to adequately protect PHI. So, what can you do to protect the integrity of your PHI?
* Produce formal documented policies and procedures for the use, disclosure, and disposal of PHI
* Train employees in PHI handling
* Implement encryption and remote wipe capabilities
* Utilize multi-factor authentication and a least-privileged approach
* Monitor and regularly audit the organization’s handling of PHI
Secure HIPAA Compliant Hosting
Are you in need of an infrastructure that can protect the health data of your organization? At Atlantic.Net, we can offer a secure HIPAA-Compliant Hosting solution. Get a free consultation today, or get started with a free trial today!
Learn more about our HIPAA-compliant web hosting and HIPAA cloud hosting solutions.
For more information, please email [email protected].
This article was updated with the most recent information on December 20, 2022.
Written by Richard Bailey
Linux, Cloud, and Lead IT Consultant with 30 years of experience. Graduate of the University of Bradford, England. Enthusiastic about Technology, Automation, and Infrastructure as Code. Passionate writer, keen to understand and disseminate as much technical knowledge as possible.
Read More About HIPAA Compliance
- HIPAA Compliance Checklist
- How to Become HIPAA Compliant
- Top Considerations for HIPAA File Storage
- HIPAA Data Storage Requirements
- Protecting e-PHI in the Cloud
- What Is HIPAA Cloud Computing?
- What Is Healthcare Hosting?
- What Is PHI?
Get a $250 Credit and Access to Our Free Tier!
Free Tier includes:
G3.2GB Cloud VPS a Free to Use for One Year
50 GB of Block Storage Free to Use for One Year
50 GB of Snapshots Free to Use for One Year
 What is a Covered Entity that handles PHI and ePHI?
What is a Covered Entity that handles PHI and ePHI?