How to Install and Configure Fail2ban on CentOS
February 1, 2016 by Editorial Team ( 450 ) under Dedicated Server Hosting
0 Comments
Verified and Tested 4/28/16
Introduction
Fail2ban is a great, wonderful service that is primarily used to stop brute forcers from accessing your system. It’s simple to install and configure and works great at deterring your basic attackers away.
This article is specifically for installation on Centos. To install and use Fail2Ban in Ubuntu and Debian, check out our how-to on that here.
In This Article
Installing and configuring Fail2Ban on CentOS
We will be performing steps below as the root user. You will just need to sudo if you are using another user. For all editing of configuration files, we will be using vi. However, you can use whichever editor you are comfortable with. This installation is performed on a clean CentOS 6.5 64bit cloud server.
Now unfortunately, fail2ban is not included in the base CentOS repo. We will need to add it so we can install it. Luckily that can be done with a simple command:
x86_64 (64bit)
rpm -Uvh http://dl.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm
i386 (32bit)
rpm -Uvh http://dl.fedoraproject.org/pub/epel/6/i386/epel-release-6-8.noarch.rpm
Once done simply run:
yum install fail2ban
It will prompt you for a yes or no for the installation. Simply hit ‘y’ on your keyboard for yes and hit enter. Fail2ban will install and we’re getting started.
Now we have to apply some configuration. The best practice when changing configuration files like this, is to always copy out the original to a backup. In this case, you can leave the original alone as fail2ban does work with a duplicate .local file also named jail. To do this, simply run:
cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
Once you’ve made that .local file, it’s time to edit it with your editor.
vi /etc/fail2ban/jail.local
Now as you’ll see when editing the file, there are A LOT of sections for you to “play” with and adjust. You will want to navigate to where the JAILS section begins. Here we are going to make a [ssh-iptables] jail with the information below. The main aspects we’ll focus on are the ignoreip, bantime, findtime, maxretry, action, and logpath.
[ssh-iptables]
ignoreip=127.0.0.1/8
bantime=600
findtime=600
maxretry = 5
enabled = true
filter =sshd
action = iptables[name=SSH, port=ssh,protocol=tcp]
sendmail-whois[name=SSH,[email protected],[email protected],sendername="Fail2ban"]
logpath = /var/log/secure
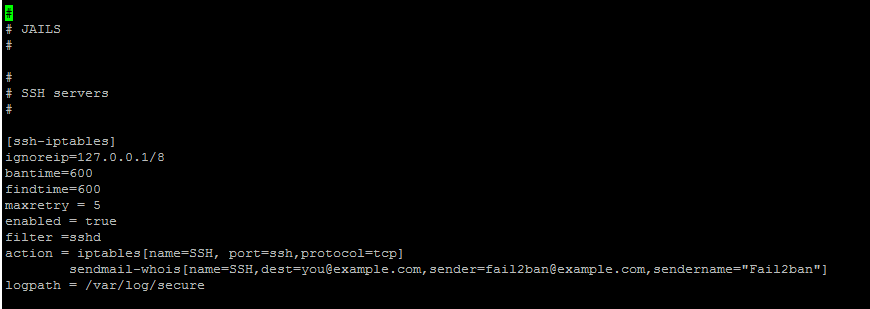
In the picture above, you will find the ignoreip. This is pretty important as you can tell fail2ban to IGNORE your IP address. This will prevent you from ever locking yourself out of your server by fail2ban. We highly recommend you add your IP address to this field. To add it, all you need to do is add a space after the 127.0.0.1/8 and put your IP.
Next you will find the bantime. As it sounds, this is how long a host is banned when triggered for banning. This is set by the number of seconds that you want that IP address blocked from your system. We recommend that if you are gunning for someone to be blocked, you set this to a high number. The default is 10 minutes. Adding a 0 will make it 6000 seconds or 100 minutes (just over an hour and a half.) That’s a good start.
The next section below that is the findtime. As it states, this is the span of time fail2ban will look at for failed attempts. The default setting here of 10 minutes is acceptable. This means fail2ban will analyze the attempts every 10 minutes and make a decision based on what it found.
Under the findtime section, you will find the maxretry. As it sounds, this is how many times you’ll allow a failure to log in within the findtime before the origin IP gets added to the ban for what you have set the bantime to be. 3 is a great number here to really catch someone attempting to get in.
Now we’ll get to enabled. This value can be either true or false. By default every Jail in fail2ban is set to false (if it’s not listed, it’s false.) To enable our jail, we will have to set this to true.
The next section we’ll look at is for action. In the “action =” section you’ll see:
iptables[name=SSH, port=ssh, protocol=tcp]
If you have not changed your SSH port, this is fine. If you have configured a custom SSH port like described in the Changing your SSH Port In CentOS article, you will want to change the port= section. For example, using a custom SSH port of 9922:
iptables[name=SSH, port=9922, protocol=tcp]
Finally we have the logpath. This will tell fail2ban what log to read for it’s decision making.
Now once you have changed this configuration to your liking, all you need to do is save the changes you did and exit the file. Once out, simply restart the fail2ban service to activate it. You may also want to run a ‘chkconfig on’ on the service to ensure it runs at boot time.
service fail2ban restart
chkconfig fail2ban on
In the future, when adding new services onto the a server (like FTP, email, etc.) make sure you check your fail2ban configuration!
Thank you for reading this article, please check out our other related articles below or learn more about our reliable dedicated server hosting solutions.
Get a $250 Credit and Access to Our Free Tier!
Free Tier includes:
G3.2GB Cloud VPS a Free to Use for One Year
50 GB of Block Storage Free to Use for One Year
50 GB of Snapshots Free to Use for One Year
