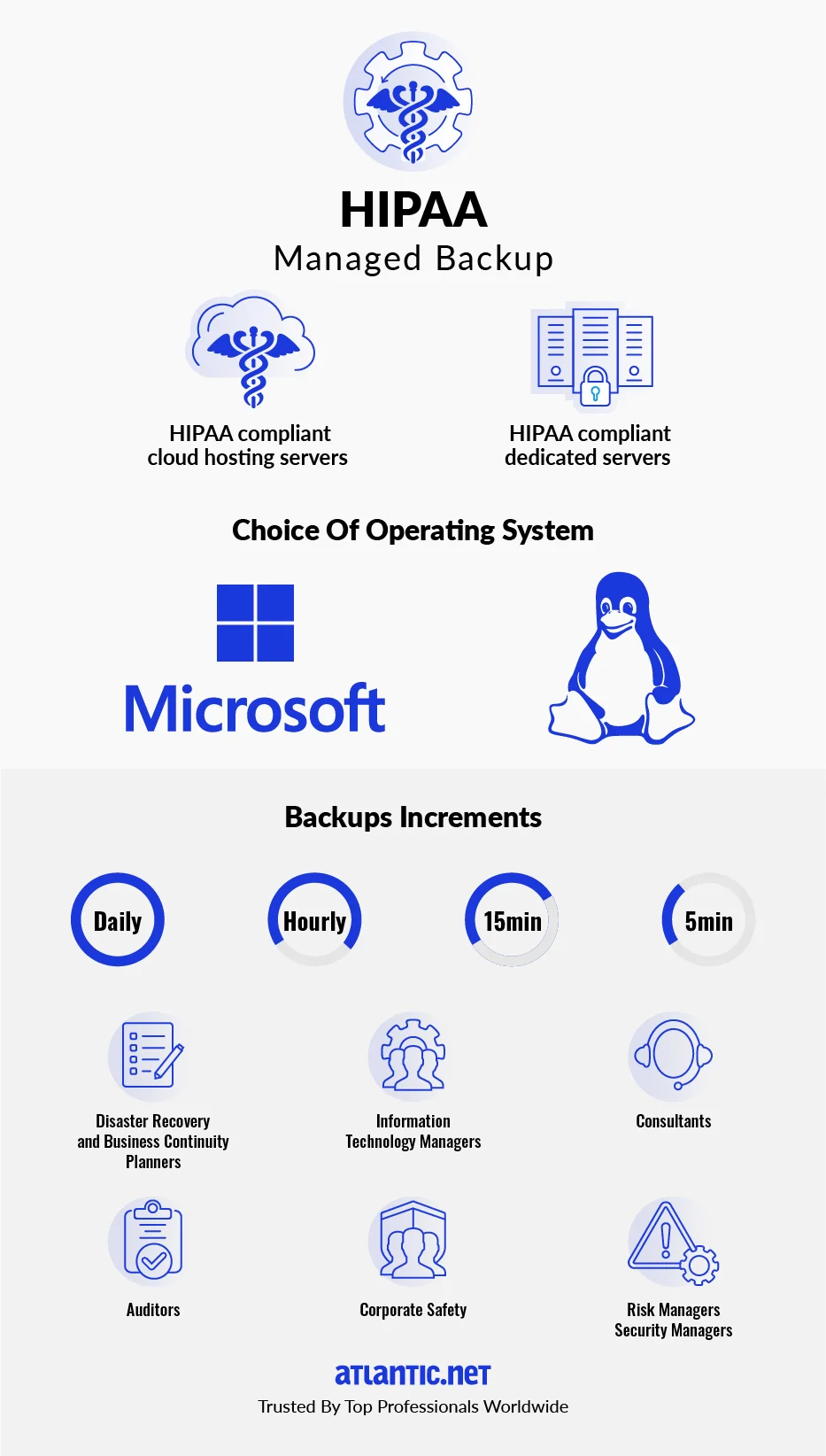
Disaster Recovery and Business Continuity for HIPAA Compliance
At Atlantic.Net, we’ve spent the last three decades preparing for the next by combining our experience, expertise, and world-class hosting infrastructure. This is to provide our clients with the most secure Disaster Recovery Hosting Solution, designed for uninterrupted business continuity.
To minimize risk and help you to quickly get back to business, Atlantic.Net offers offsite backup and replication of your mission-critical data away from the primary facility. This ensures smooth data recovery in the event of a local outage due to a regional disaster. Our Disaster Recovery Solutions are ideal for privacy, security, and compliance, which requires adherence to the strictest government regulations.