What Is HIPAA-Compliant Hosting?
HIPAA-compliant hosting is a web hosting solution that meets and exceeds the required administrative safeguards, physical safeguards, and technical safeguards mandated by the HIPAA regulations of 1996 (Health Insurance Portability and Accountability Act). Managed service providers, HIPAA-covered entities like healthcare providers, and relevant third parties are bound by HIPAA regulations to protect and uphold patient data integrity. The web, database, or storage solution could either be cloud-based or run on a dedicated server with the necessary security features. A service provider offering HIPAA-compliant Linux or Windows hosting must sign a Business Associates Agreement.
HIPAA-Compliant Hosting Services and Solutions by Atlantic.Net
HIPAA-Compliant Hosting by Atlantic.Net™ is SOC 2 and SOC 3 certified, HIPAA and HITECH audited, and designed to secure and protect critical health data, electronic protected health information (ePHI), and records. We are audited by a qualified and an independent third-party CPA firm to validity of our operational controls and compliance services.
HIPAA Compliant Website Hosting
Our HIPAA Compliant Web Hosting Platform is secured to industry standards, providing a highly durable, feature-rich solution, powered by the latest tech, offering breakneck performance - available in both dedicated and cloud server environments and backed by our 100% uptime SLA.
Need Help?
HIPAA-Compliant Cloud Hosting
Security, scalability, high-speed data transfers, and performance are the focus of our Cloud Hosting Solutions. Atlantic.Net’s HIPAA Cloud solutions offer fast provisioning, ongoing management, and round-the-clock monitoring.
Looking For a HIPAA Compliant Server?
Atlantic.Net provides customized HIPAA hosting plans to meet all your HIPAA hosting needs. The ongoing monthly cost greatly depends upon variables like security services, and server specifications. Here are a few standard Linux and Windows HIPAA hosting pricing plans and packages:
HIPAA Compliance Hosting Plans & Cost - Linux and Windows
HIPAA Developer
Linux
Managed Cloud Server
$320.98 Per Month
4 vCPU
8GB RAM
160GB SSD Storage
10TB Monthly Data Transfer
- Fully Managed Firewall
- Business Associates Agreement
- Onsite Daily Backups
- Server Management
- Bi-Weekly Vulnerability Scans
- cPanel 5 Account License
- 4 Hours of Migration Service
- Intrusion Prevention Service
- Multi-Factor Authentication
- Off-site Daily Backups
- Trend Micro Security Suite*
- Network Edge Protection
- Load Balancing
HIPAA Business
Linux
Managed Cloud Server
$518.97 Per Month
6 vCPU
16GB RAM
320GB SSD Storage
10TB Monthly Daily Transfer
- Fully Managed Firewall
- Business Associates Agreement
- Onsite Daily Backups
- Server Management
- Bi-Weekly Vulnerability Scans
- cPanel 5 Account License
- 4 Hours of Migration Service
- Intrusion Prevention Service
- Multi-Factor Authentication
- Off-site Daily Backups
- Trend Micro Security Suite*
- Network Edge Protection
- Load Balancing
HIPAA Enterprise
Linux
Managed Cloud Server
$692.64 Per Month
8 vCPU
32GB RAM
640GB SSD Storage
10TB Monthly Daily Transfer
- Fully Managed Firewall
- Business Associates Agreement
- Onsite Daily Backups
- Server Management
- Bi-Weekly Vulnerability Scans
- cPanel 5 Account License
- 4 Hours of Migration Service
- Intrusion Prevention Service
- Multi-Factor Authentication
- Off-site Daily Backups
- Trend Micro Security Suite*
- Network Edge Protection
- Load Balancing
HIPAA Developer
Windows
Managed Cloud Server
$319.98 Per Month
4 vCPU
8GB RAM
160GB SSD Storage
10TB Monthly Data Transfer
- Fully Managed Firewall
- Business Associates Agreement
- Onsite Daily Backups
- Server Management
- Bi-Weekly Vulnerability Scans
- Windows License
- 4 Hours of Migration Service
- Intrusion Prevention Service
- Multi-Factor Authentication
- Off-site Daily Backups
- Trend Micro Security Suite
- Network Edge Protection
- Load Balancing
HIPAA Business
Windows
Managed Cloud Server
$539.97 Per Month
6 vCPU
16GB RAM
320GB SSD Storage
10TB Monthly Daily Transfer
- Fully Managed Firewall
- Business Associates Agreement
- 4 Hours of Migration Service
- Onsite Daily Backups
- Server Management
- Bi-Weekly Vulnerability Scans
- Windows License
- Intrusion Prevention Service
- Multi-Factor Authentication
- Off-site Daily Backups
- Trend Micro Security Suite
- Network Edge Protection
- Load Balancing
HIPAA Enterprise
Windows
Managed Cloud Server
$757.64 Per Month
8 vCPU
32GB RAM
640GB SSD Storage
10TB Monthly Daily Transfer
- Fully Managed Firewall
- Business Associates Agreement
- 4 Hours of Migration Service
- Onsite Daily Backups
- Off-site Daily Backups
- Server Management
- Bi-Weekly Vulnerability Scans
- Windows License
- Intrusion Prevention Service
- Multi-Factor Authentication
- Trend Micro Security Suite
- Network Edge Protection
- Load Balancing
HIPAA Custom
Larger Complex Deployments
Custom VM Sizes
- Fully Managed Firewall
- Business Associates Agreement
- Onsite Daily Backups
- Bi-Weekly Vulnerability Scans
- cPanel License
- Linux or Windows License
- Intrusion Prevention Service
- Multi-Factor Authentication
- Off-site Daily Backups
- Trend Micro Security Suite
- Network Edge Protection
- Load Balancing
Looking for HIPAA compliant hosting, but do not know where to start?
We can help with a customized solution to meet your business requirements.
IT Architecture Design,
Security, & Guidance.
Flexible Private, Public, &
Hybrid Hosting.
Full suite of Security
Services
- Trend Micro security package is available for an additional cost.
- Migration services under the HIPAA Business and HIPAA Enterprise plans are free for up to four hours and billed at $160.00 per hour after the first four hours.
Need Help?
HIPAA Cloud Hosting and Storage
HIPAA-Compliant Cloud Hosting and Storage should be audited and certified to the required standards of the HIPAA Security Rule by an independent third party.
The service is architected for enhanced privacy and ultra-secure access controls; the result is all the benefits of the cloud in a consumable, compliant service.
HIPAA Cloud Storage is ideal for mission-critical applications without compromising speed, security, and reliability, great for storing large datasets, file transfers, file storage, online storage, imaging, and health records requiring enhanced encryption.
Secure Block Storage (SBS)
Atlantic.Net’s user-friendly, highly redundant, easily accessible, and scalable Secure Block Storage (SBS) is ideal for a mission-critical application platforms requiring robust and scalable storage.
Need to run large queries on datasets? No problem! SBS has low latency and high performance for any HIPAA-compliant cloud storage workload.
Click here to learn more about our Secure Block Storage (SBS).
HIPAA-Compliant Database Hosting
Need a secured, reliable, and high-performance database? We’ve got you covered!
Our secure and efficient solutions work with a variety of SQL platforms, both proprietary and open source. Whether you're hosting sensitive healthcare records, AI applications, or large data sets and images, rest assured your databases are backed by our 100% uptime SLA!
Here are the databases we support:
Microsoft SQL (MS SQL):
Microsoft SQL Server can support small or large data warehouses in a user-friendly package. Data is secured with Always-On encryption technology, row-level security, dynamic data masking, transparent data encryption (TDE), and robust auditing.
MySQL:
MySQL features easy access and interaction with the server. Triggers, stored procedures, and views enhance development efficiency and productivity. MySQL is faster, cost-effective, and reliable, with a solid security layer protecting sensitive data from intruders.
Windows HIPAA-Compliant Hosting
Need Windows? No problem!
Our HIPAA-Compliant Windows Hosting supports all versions of:
- Windows Server 2022
- Windows Server 2019
- Windows Server 2016
Running older versions of Windows? We can still help. Get in touch today!
Linux HIPAA-Compliant Hosting
Need Linux? No problem!
In addition to FreeBSD and Arch Linux, our HIPAA-Compliant Linux Hosting supports:
- Ubuntu
- Debian
- Rocky Linux
- CentOS
- Oracle Linux
- Fedora and many more!
One-Click HIPAA-Compliant
Apps
These preconfigured apps start in seconds with only a few mouse clicks. Apps include:
- LAMP/LEMP
- WordPress
- Nextcloud
- MySQL
- cPanel/WHM
HIPAA-Compliant Hosting Demo:
Whether you need comprehensive, fully managed HIPAA-compliant hosting services for HIPAA servers or unmanaged hosting solutions, we can assist with all your HIPAA compliance hosting needs. Our high-performance HIPAA-Compliant Website, Database, and Storage servers are available as both Dedicated Servers and Cloud-based HIPAA-compliant environments, backed by our 100% uptime SLA.
Watch a brief video demonstrating our HIPAA hosting solution capabilities.
HIPAA Hosting Features
Business Associate Agreement
Intrusion Prevention Service
Fully Managed Firewall
Vulnerability Scans
File Integrity Monitoring
Anti-Malware Protection
SSL Certificate
Log Management System
Multi-Factor Authentication
Trend Micro Deep Security
Encrypted Backup
Encrypted VPN
Encrypted Storage
Network Edge/DDoS Protection
Business Associate Agreement (BAA) Available with All HIPAA Hosting Plans
Service Organization Control
Ensures internal controls and best practices for physical security, availability, processing integrity, confidentiality, and privacy.
HIPAA Audited
Ensures our processes, policies, data centers, facilities, and hosting solutions comply with the latest HIPAA audit protocols.
HITECH Audited
Stringent testing to comply with HITECH Act security standards, policies, and protocols.

Why Choose Atlantic.Net?
- HIPAA and HITECH Audited
- Celebrating 30 years of excellence
- 100% Uptime Service Level Agreement
- World-Class Data Center Infrastructure
- High Touch Approach
- Emphasis on Security and Compliance
- Stability and Strategic Advantage
- Industry Leading Certifications
- Specialists at HIPAA-Compliant Hosting
- 24/7 Support via Phone and Email
- Industry Awards and Partnerships
- Trend Micro Deep Security Suite
- Fully Managed Firewall Appliance
- Multi-Factor Authentication
- Load Balancing
- Encrypted Backup, Storage & VPN
- Fully Managed Daily Backups
- Log Inspection System
- GDPR Ready
- PCI/DSS Ready
- NIST Certified Data Centers
- EU/US Privacy Shield Compliant Data Centers
Start Your HIPAA Project With a
Fully Audited HIPAA Platform Today!
HIPAA-Compliant Server & Storage, Encrypted VPN, Security Firewall, Offsite Backup, Disaster Recovery, Business Associates Agreement (BAA) & more!
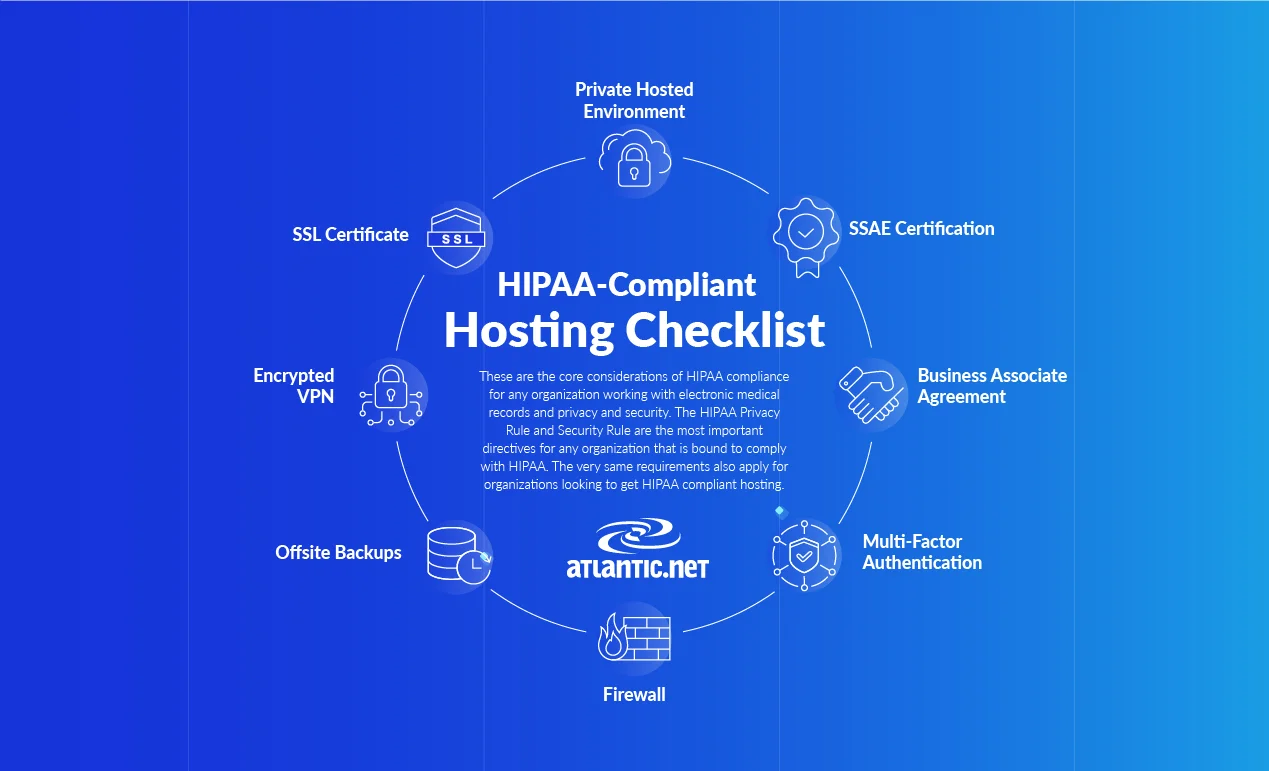
HIPAA-Compliant Hosting Requirements Checklist
Implementing HIPAA compliance can be complicated and requires a clear understanding or compliance and technology. HIPAA compliance hosting involves integrating cloud server hosting solutions with security and managed services to achieve HIPAA compliance.
The end solution must include a Business Associates Agreement.
HIPAA Hosting Requirements
Atlantic.Net's HIPAA Hosting meets all the requirements of HIPAA compliance in accordance with the HIPAA Privacy Rule and Security Rule.
Here are the nine elements which we provide as a part of our HIPAA Hosting offering:
Need Help?
Firewall
A fully implemented firewall in your server environment is a must to meet HIPAA server requirements. Atlantic.Net's servers combine perimeter and server-side firewalls with solutions specifically designed to protect against security threats. Most importantly, we deploy, maintain, and manage the firewalls.
Encrypted VPN
Your virtual private network (VPN) must have strong encryption mechanism. Atlantic.Net's ensures that your VPN is encrypted to meet the HIPAA requirements and safeguards.
Onsite and Offsite Backups
HIPAA requires that you back up data locally and externally (onsite and offsite). Local onsite backups ensure quick recovery times if something goes wrong, while the offsite backups can significantly help after a catastrophic failure. On and offsite backups from Atlantic.Net can help you meet this need.
Multi-Factor Authentication
Multi-factor authentication involves the verification of user identity using a combination of factors like a piece of information that only the user knows, authenticate with a secure application, text message, or a biometric factor. Atlantic.Net offers multi-factor authentication solutions to protect your environment from unauthorized access.
Private Hosted Environment
Your server should be set up in a way that it is isolated from other machines on the platform. Atlantic.Net's experienced engineers can help you to properly set up a private infrastructure and help avoid missteps. Ensuring your data and environments are properly segmented from other machines is extremely important for the integrity of your data.
SSL Certificates
For HIPAA compliance, you need secure sockets layer (SSL) certificates established for any domains and subdomains hosting healthcare information or where sensitive ePHI is accessed. Any part of your site that needs login credentials should have an SSL.
SOC 2 TYPE II and SOC 3 TYPE II Certifications
Atlantic.Net features heightened security with fully-managed firewalls, encrypted VPNs, storage, and backup, and intrusion detection and prevention systems, all backed by an infrastructure that has received SOC 2 and SOC 3 compliant reports. The audit for the reports is based on the AICPA guidelines, including the Trust Service Principles. These tests of operating effectiveness include controls relevant to security and availability principles. These reports replaced the previous Statement on Auditing Standards No. 70 reports, as the SAS 70 standard has been retired.
HIPAA Audited
Atlantic.Net provides a secure environment that offers medical companies and patients online protection through its award-winning HIPAA-Compliant Server solutions in an environment built to safeguard ePHI. A HIPAA server alone does not make you HIPAA-compliant. Compliance is determined by adherence to the privacy and security rules outlined by HIPAA. HIPAA servers only address one aspect of those requirements. You are still required to meet administrative and technical specifications of the HIPAA Security Rule to be compliant.
Business Associate Agreement (BAA)
If you use any outside entity to handle ePHI, including a server infrastructure company, you must have a Business Associate Agreement (BAA) signed with that organization to ensure that your business associate meets their HIPAA responsibilities. That document does not relieve you of your responsibilities related to HIPAA, but delineates the external organization's role, liability for breaches, and more. Atlantic.Net offers a BAA as a standard part of the HIPAA hosting offering.
Partnering with a trusted HIPAA-compliant cloud hosting provider such as Atlantic.Net can take the hassle out of compliance.
Safeguard sensitive patient data with Atlantic.Net's HIPAA-compliant hosting solutions. Our world-class infrastructure and expert support ensures peace of mind for your Healthcare organization. Contact us to discuss your HIPAA requirements. For faster application deployment, free IT architecture design, and assessment, call 888-618-DATA (3282) or email us at [email protected].
HIPAA Hosting Requirements Infographic
Looking For HIPAA-Compliant Hosting?
We Can Help With A Free
Assessment.
IT Architecture Design, Security,
& Guidance.
Flexible Private, Public, &
Hybrid Hosting.
24x7x365 Security, Support, &
Monitoring.
Need Help?
HIPAA Hosting FAQs
HIPAA compliance is difficult for HIPAA-compliant hosting providers to achieve as there are many physical and technical safeguards that a HIPAA-compliant cloud solutions infrastructure must fulfill in order for a cloud service provider to meet HIPAA requirements to safeguard protected health information (PHI). For this reason, a free web hosting service that can ensure HIPAA compliance according to the Privacy and Security Rules may not be an option.
We offer very competitive pricing for HIPAA-compliant server hosting services from eight regions in the USA, Canada, United Kingdom, and Singapore.
A HIPAA-Compliant hosting environment requires specialist configuration, management, and upkeep. Our HIPAA Hosting packages start from only $297.98 per month. The cost of HIPAA-compliant services depends on what is in scope. For example, HIPAA-compliant email services could be substantially less than a fully HIPAA-compliant IT environment. Costs are incurred because extra steps are needed to safeguard data, meet regulations, and undergo audits within HIPAA-compliant environments.
Your data is the most valuable asset of your organization and opting for a cheap HIPAA hosting may sound good but in the long run might not be a smart idea. You should want to ensure the provider is fully audited and can sign a BAA. HIPAA hosting solutions are worth the cost, especially considering legal liabilities for healthcare providers and their business associates when patient data is breached. In this case, cheapest is not the best - you need quality support and expertise.
We always recommend consulting legal advisors if you're unsure whether HIPAA legislation applies to your business as a covered entity or a business associate.
Generally, if you process or store protected health information (PHI) that can identify a patient, then HIPAA rules apply, and you'll need a HIPAA-compliant hosting solution to store electronic protected health information in a public cloud or on dedicated servers.
If patient data is anonymized, the rules can vary; once again, seek legal advice if you are unsure.
HIPAA cloud hosting offers strategic advantages and alleviates headaches for our customers in the healthcare industry.
A HIPAA-compliant hosting solution ensures that all the physical, administrative, and technical safeguards of HIPAA are met with your Atlantic.Net services as long as you consume those services appropriately and maintain proper safeguards on your side.
You can find many more details on the advantages here.
Certifications help showcase your provider’s expertise and tenacity in maintaining the best HIPAA-compliant environment. Look for SOC 2/SOC 3 certifications and HITECH and HIPAA Audited partners who offer a business associate agreement (BAA).
To review all Atlantic.Net certifications and partnerships, click here.
Managed hosting providers aren't allowed to falsely advertise HIPAA-compliant services; however, the extent of the HIPAA audit HIPAA hosting companies offer to get your team to full HIPAA compliance will vary. HIPAA regulations are federal law. Breaching HIPAA could result in hefty fines. While some vendors might say they are "compliant," responsibility remains with the HIPAA-covered entity to ensure that they are engaging with truly compliant business associates. The only way to ensure this is to have a solid BAA in place and perform an audit of their HIPAA-compliant hosting solutions.
Some competitors say they offer HIPAA-compliant hosting solutions, but they might only be talking about a server or a specific part of their service; for example, if they advertise HIPAA-compliant email services but don't state that their other services are HIPAA-compliant, check for yourself. It is best practice to perform an audit of the environment to ensure no assumptions are made between the supposedly HIPAA-compliant hosting providers offering the platform that powers healthcare technology systems and the healthcare organizations themselves.
For a covered entity in the healthcare industry, one significant advantage of outsourcing hosting is the additional optional managed services. Managed services, such as backups, server management, an IPS, vulnerability scans, anti-malware, and network security, can be bolted onto a hosting services package. For detailed information about the managed services available to the healthcare industry from Atlantic.Net check out this page.
While databases are not inherently HIPAA-compliant, cloud hosting providers can deliver the cloud services and database management services required to make compliance easy. HIPAA legislation requires organizations to implement the following to ensure compliance:
- Access control
- Data encryption
- Audit logging
- User authentication
- Data backups and disaster recovery
- Business Associate Agreements (BAA)
- Fully encrypt your data at rest and in transit
- Harden the operating system and close any not used ports
- Enforce unique user authentication and multi-factor authentication
- Maintain audit logs
- Perform regular, fully encrypted server backups
- Assign appropriate user roles and privileges
- Perform vulnerability scans regularly to ensure no gaps are missed
- Utilize anti-malware, file scanners, network scanners for ongoing HIPAA compliance monitoring to ensure no breaches occur
Merely securing a signed BAAs will not guarantee healthcare organizations' compliance with HIPAA guidelines. When developing HIPAA-compliant cloud solutions, a Covered Entity and its Business Associates must work closely together to ensure that they comply with HIPAA legislation, implementing key security features, such as physical security policies, multi-factor user authentication, industry-standard encryption, and activity monitoring (some web hosting companies offer HIPAA compliance monitoring).
Start Your HIPAA Project With a
Fully Audited HIPAA Platform Today!
HIPAA-Compliant Server & Storage, Encrypted VPN, Security Firewall, Offsite Backup, Disaster Recovery, Business Associates Agreement (BAA) & more!
Millions of Cloud Deployments Worldwide

® Each logo is the registered trademark of its respective company.
Award-Winning Service

Our Data Center Certifications

In The News

Our Technology Partners

Dedicated to Your Success

- Jason Coleman
VP of Information Technology, Orlando Magic
"After evaluating a range of managed hosting options to support our data operations, we chose Atlantic.Net because of their superior infrastructure and extensive technical knowledge."

- Erin Chapple
General Manager for Windows Server, Microsoft Corp.
"Atlantic.Net’s support for Windows Server Containers in their cloud platform brings additional choice and options for our joint customers in search of flexible and innovative cloud services."
Share Your Vision With Us
And We Will Develop a Hosting Environment Tailored to Your Needs!
Contact an advisor at 866-618-DATA (3282), email [email protected], or fill out the form below.
Don't just take our word for it: Cyber Defense Magazine recognized Atlantic.Net as "Most Innovative Cloud Hosting Provider" in the 2025 Global Infosec Awards.