Distributed denial of service (DDoS) attacks have been happening for years, but have become steadily more prominent among enterprise IT considerations. This is in large part due to the increasing amount of damage inflicted by DDoS attacks, which is caused by both the increasing power and sophistication of the attacks, and also the critical importance of IT systems availability to enterprises.
What Is a DDoS Attack?
A DDoS attack is a coordinated flood of traffic or data sent from many computers and internet connections to a single destination system in order to overwhelm it. The attack can be made against different parts or “levels” of the network, taking up all of the connections, bandwidth, or processing power available. DDoS attacks can cause a general system failure or take down a certain application or service.
The Impact of DDoS Attacks
There are approximately 2,000 DDoS attacks every day, according to Arbor Networks, and research suggests that roughly one in three downtime incidents are caused by them. The cost of that downtime is severe, but the cost of restoring system functionality can be even higher. Additionally, there are indirect costs, such as to reputation, and lost staff time. The Ponemon Institute estimates that the average cost per incident, not including reputational damage, is over $125,000.
Hackers execute these costly attacks for a variety of reasons, including for gain through extortion or sabotage, but also “hacktivism,” or to test or prove their capacity to carry them out.
A DDoS attack against DNS provider Dyn that took down some of the internet’s most popular sites in October 2016 showed not just the scale the problem has reached, but also the scope of “collateral damage” caused by the attacks, and the reality that businesses can face them even without being targeted. High profile attacks of this kind can give people the impression that the hackers are winning, no-one is safe, and the situation is hopeless. There are things every company can do, however, to avoid or minimize the damage of DDoS attacks.
How Does DDoS Work?
To carry out a DDoS attack, the hacker typically builds a network of many computers that can be controlled remotely by infecting them with malware. The network is known as a “botnet,” and it provides the necessary volume of requests or data to overwhelm the attack target. Any device which connects to the internet can be used, and IoT devices are becoming popular for use by hackers in botnets.
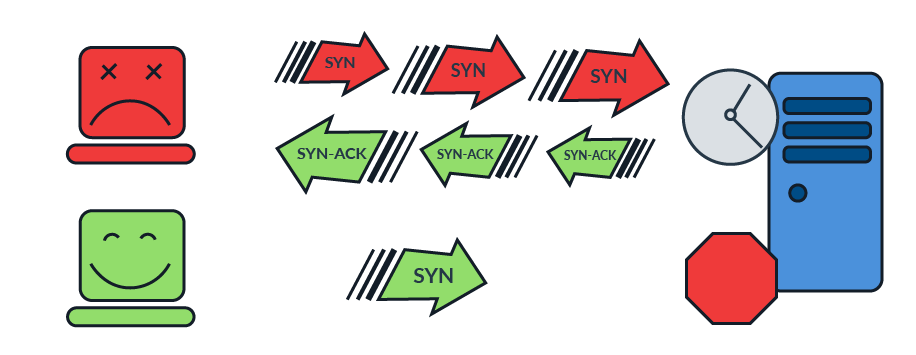
What is a DDoS
The frequency of DDoS attacks has significantly increased in part due to the availability of attack kits on the dark web. Hackers can purchase tools from secret forums and online markets, allowing them to quickly and easily build enormous botnets. Hackers also sell individual attacks as a service on the dark web.
With the botnet constructed and a target chosen, the hacker carries out the attack.
Types of Attacks
The most common types of attacks include volumetric attacks, protocol attacks, and application attacks. Each type of attack basically targets a bottleneck somewhere in the network, which means that preventing and mitigating them begins with identifying the different kinds of potential bottlenecks present in your network and addressing them.
Volumetric Attacks
A volumetric attack is an attempt by a hacker to fill the victim’s bandwidth, most often with a large volume of a certain type of data packet sent to the victim. In the most common version, the hacker simultaneously sends out a batch of User Datagram Protocol (UDP) packets that appear to come from the victim. The computers that receive the packets send responses, which are larger, to the victim, until the victim’s network is overwhelmed.
Protocol Attacks
Protocol attacks are also known as state-exhaustion attacks, and take advantage of the way computers communicate. The victim’s network often ends up waiting for a response that never ends up coming. This ends up taking a connection spot from the maximum number of possible connections a service is set to accept.
Application Attacks
Application attacks target a vulnerability in a certain program, using behavior like downloading that can resemble normal human traffic, and therefore can go undetected until they have succeeded in taking the down the server. For this reason, protecting against them requires proactive monitoring to distinguish the attack traffic from real visitor traffic.
DDoS Success: Preventing Attacks
There are a number of steps enterprises can take to guard against DDoS attacks. First, the network environment can be built or adjusted to avoid vulnerabilities and bottlenecks, which are also known in networking as “single points of failure.” Next, DDoS detection and mitigation tools, like firewalls and intrusion detection/prevention appliances can be deployed to prepare the enterprise. Finally, monitoring the network and managing its updates and backups keeps the system healthy and allows for early warning of an attack.
What Makes Networks Resistant to Attacks?
Networks that are served from different data centers and that have different routes for traffic to travel tend to be more resistant to DDoS attacks than those served from one building, because affected areas can be avoided. Every environment should have at least one dedicated firewall in front of any applications sensitive to attacks. Other important steps include employing technologies like intrusion prevention and vulnerability scans. Making sure these protections are available for your network is part of choosing the right host.
With the right protections, even large, sophisticated DDoS attacks can be mitigated. Google’s Project Shield protects websites of potential DDoS targets like journalists and non-governmental organizations. Google filters traffic, and also saves copies of websites to different locations and serving them from there, leveraging its massive scale. It has mitigated some of the largest attacks ever recorded, including one on cybersecurity researcher Brian Krebs in September 2016.
Software-as-a-Service company ShareSafe had experienced DDoS attacks prior to selecting Atlantic.Net, and was down for up to four hours, according to ShareSafe CTO and CSO John Beck. After switching to Atlantic.Net, the company was hit with two DDoS attacks last year, and on both occasions, its services were restored within five minutes.
Steps to Prevent DDoS Downtime
There are some good resources available on the web for enterprises looking for cybersecurity best practices to prevent and minimize damage from DDoS attacks. One good starting point is a guide from IBM’s Security Intelligence, which provides steps for securing your network and planning ahead for what you will do under attack. The guide identifies several features of Atlantic.Net’s security protection as important steps to take against DDoS attacks, including vulnerability scans and intrusion prevention, which can be used to build a customized solution for your business.
Letting Atlantic.Net’s cybersecurity experts architect a solution can help ensure its effectiveness. Hosting environments built with load balancing and failover capabilities help maintain consistent operation while under attack, and for cases of prolonged DDoS attacks which take down a firewall, failover firewalls are also available. In an environment with multiple load balanced nodes, requests can still be served by directing them away from traffic blocked during the attack.
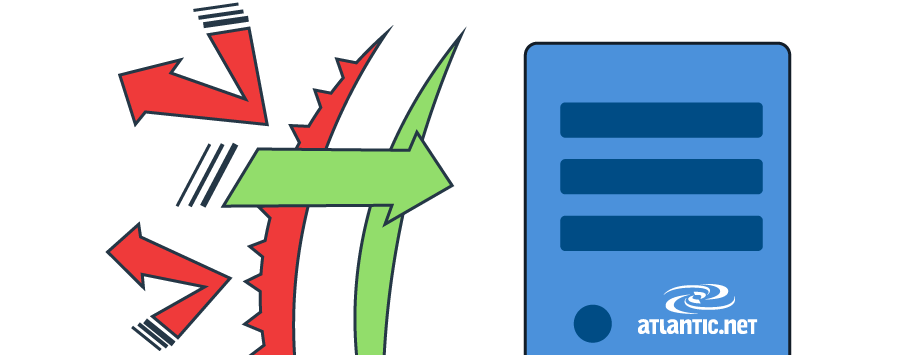
A DDoS attack is a coordinated flood of traffic or data sent from many computers and internet connections to a single destination system in order to overwhelm it.
Atlantic.Net’s Network Operations Center monitors the networks 24/7 to block or mitigate hazardous traffic. Operating out of six data centers, Atlantic.Net provides the geographic distribution and diversity of traffic routes necessary to avoid areas under attack, and keep your network and website up.
The variety of different DDoS attacks, their frequency, and the damage they frequently inflict can be intimidating, and the methods of dealing with them are necessarily multi-faceted. Hosts like Atlantic.Net, and security providers like Atlantic.Net partner Trend Micro, however, have the experience and knowledge to help. Leverage that help, and you can prepare your business to stay online, minimize damage, and get on with what you do best.
Atlantic.Net’s Managed Services
With Atlantic.Net’s Managed Services, VPS Hosting and custom solutions, you get what your business needs to be protected from modern-day cybersecurity threats, all backed by decades of expert-level experience. Everything is custom-built and set up to suit your needs, from our Atlantic.Net Managed Firewall and Intrusion Detection/Prevention Systems to Atlantic.Net’s Edge Protection and Load Balancing. Contact our friendly and knowledgeable Sales team today for more information and to find out how to get started protecting your business.