HIPAA and PCI-DSS are two sets of regulatory guidelines that govern the way an organization handles certain types of data. This includes how data is saved, used, and accessed by enterprise information technology (IT) systems. Failure to conform to the appropriate regulations puts data resources at risk and can lead to substantial financial penalties along with long-term negative repercussions to a business’s reputation.
When contracting with a web hosting provider, you need to know if you are bound by either or both guidelines and if your vendor offers compliant systems and storage. Fortunately, Atlantic.Net is compliant and audited for HIPAA, HITECH, and PCI-DSS requirements and maintains SOC2 and SOC3 certifications that are performed by a third party to verify Atlantic.Net’s compliance.
 What are HIPAA and PCI -DSS Compliance Standards?
What are HIPAA and PCI -DSS Compliance Standards?
These sets of regulatory guidelines were developed to address the needs of two very different industries. The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is focused on protecting the personal data of individuals who interact with healthcare providers. The Payment Card Industry Data Security Standard (PCI-DSS) was designed to protect the information of credit cardholder data.
Companies handling health-related data are bound to adhere to HIPAA guidelines. PCI-DSS regulations must be followed by companies processing credit card data. In many cases, both sets of standards may apply to the same company, for example with a healthcare provider that accepts credit card payments.
Compliance with HIPAA or PCI-DSS guidelines is mandatory for businesses in these industries. There is no opting out, and inadvertent non-compliance is no excuse nor a remedy for potential penalties. Let’s take a look at how these regulations were established.
 HIPAA
HIPAA
The Health Insurance Portability and Accountability Act of 1996 set the original guidelines that organizations need to follow to guard protected health information (PHI) and electronic protected health information (ePHI). The Health Information Technology for Economic and Clinical Health (HITECH) Act of 2009 also plays a role in HIPAA IT compliance.
The HIPAA Security Rule contains the standards that must be applied to safeguard and protect electronically created, accessed, processed, or stored PHI (ePHI) when at rest and in transit. Some of the following safeguards are required while others are categorized as addressable to provide for flexibility in implementing the controls.
Technical safeguards are:
- Encrypting data that travels beyond internal firewalls to NIST standards;
- Implementing a means of access control for PHI and ePHI;
- Introducing audit controls and activity logs to the environment.
Physical safeguards apply to physical access to ePHI regardless of where it is stored. Required physical safeguards are:
- Implementing policies to protect workstations that access ePHI;
- Implementing policies directed at the use of ePHI on mobile devices and its removal when an individual leaves the organization.
- Implementing policies that secure where the ePHI is stored and also disposed of in accordance of best practices.
Administrative safeguards are designed to ensure an organization is taking the proper steps to maintain the privacy and security of ePHI. Required administrative safeguards are:
- Conducting risk assessments to determine how ePHI is used and how breaches could occur;
- Developing a risk management policy and HIPAA compliant policies and procedures that includes sanctions for employees who fail to comply with HIPAA guidelines;
- Developing a contingency plan to protect ePHI in case of an emergency;
- Restricting third-party access to ePHI.
 PCI-DSS
PCI-DSS
The development of the PCI-DSS standards began through the efforts of founding members American Express, Discover Financial Services, JCB International, MasterCard, and Visa. The group introduced PCI-DSS 1.0 in December of 2004 to address the risks of fraud in the credit card industry. In 2006 the PCI Security Standards Council (PCI SSC) was created and continues to oversee the evolution of the guidelines.
There are 12 general steps that may each be comprised of multiple activities required to conform to entry-level PCI-DSS standards. They are:
- 1-Install and maintain a firewall to protect cardholder data;
- 2-Change all vendor-supplied and default passwords;
- 3-Protect stored cardholder data;
- 4-Encrypt transmission of cardholder data over open networks;
- 5-Deploy and update anti-virus software;
- 6-Develop and maintain secure systems;
- 7-Restrict access to cardholder data on a need-to-know basis;
- 8-Assign a unique ID to all computer users;
- 9-Restrict physical access to cardholder data;
- 10-Track and monitor access to networks and data;
- 11-Regularly test security systems and procedures;
- 12-Maintain a policy that addresses data security for employees and contractors.
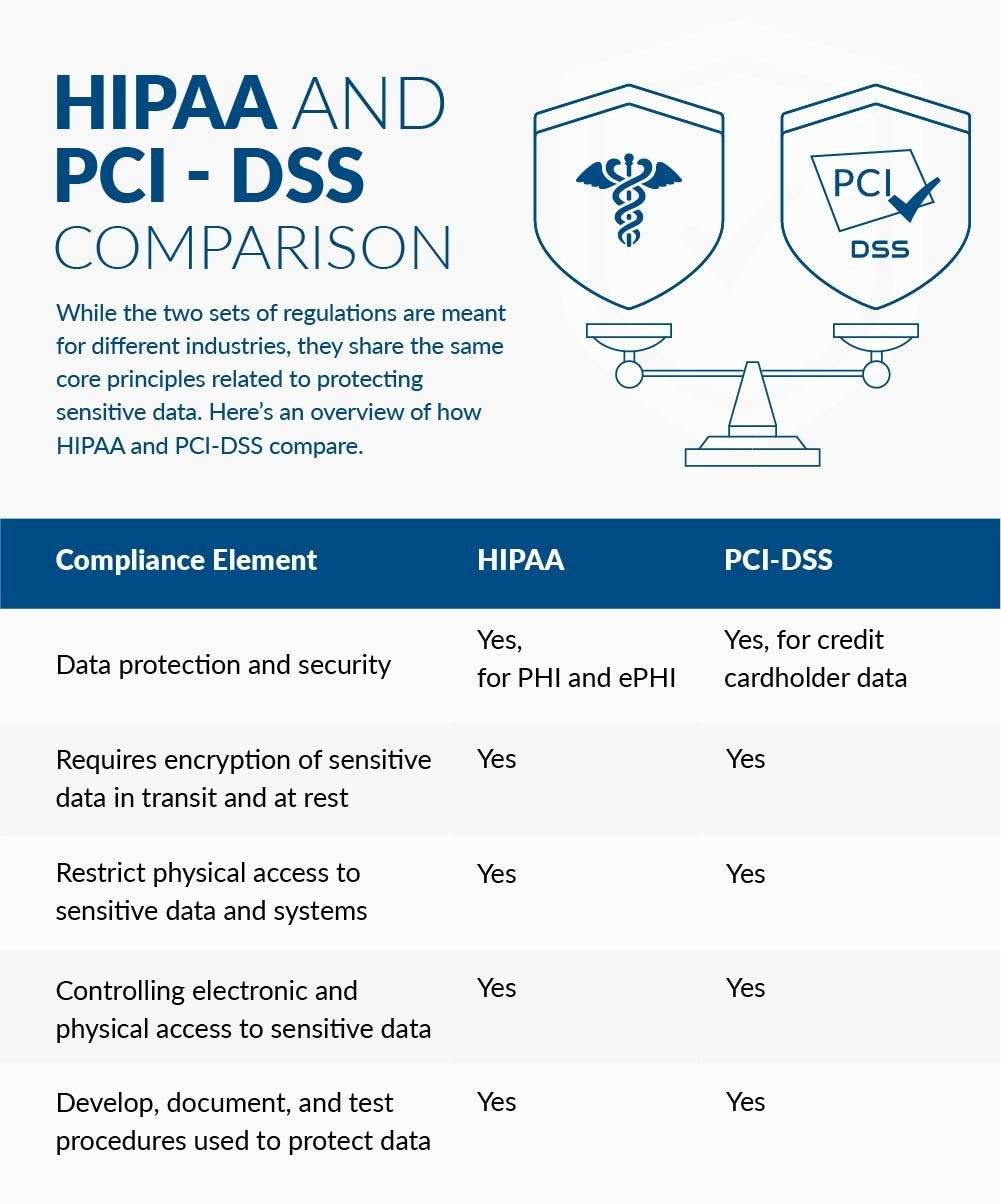
 A Comparison of HIPAA and PCI-DSS
A Comparison of HIPAA and PCI-DSS
While the two sets of regulations are meant for different industries, they share the same core principles related to protecting sensitive data. Here’s an overview of how HIPAA and PCI-DSS compare.
 How to Ensure HIPAA and PCI Compliance
How to Ensure HIPAA and PCI Compliance
A growing number of organizations are required to meet PCI-DSS and HIPAA compliance standards, which means implementing more controls, preparing documentation, and assessment efforts. This can be easily achieved by hiring skilled external auditors that can implement framework mapping to combine PCI and HIPAA compliance efforts, limit assessments to a single scope, and cut out redundant work,” according to I.S. Partners.
Organizations can obtain certification from licensed third parties to verify their compliance with HIPAA or PCI-DSS guidelines. This is commonly done via Service Organization Control (SOC) 2 and 3 certifications.
What is SOC?
SOC reports are internal control reports on the services provided by a service organization. The reports furnish important information to potential customers about the risks of using the outsourced services.
- SOC 1 reports concentrate on an enterprise’s controls over financial reporting. Companies operating in the financial services industry rely on SOC 1 reporting.
- SOC 2 reports evaluate an organization’s information systems relating to their security, availability, processing integrity, confidentiality, and privacy. These elements are collectively known as the Trust Services Criteria. A SOC 2 report has restricted access and is only used by an organization and the customers that use their systems.
- SOC 3 reports also provide information based on the Trust Services Criteria but with a very important difference. SOC 3 reports can be freely distributed and used for marketing purposes to demonstrate the system compliance to prospective clients.
 Check with your provider
Check with your provider
Simply because your chosen web hosting provider offers HIPAA or PCI-DSS complaint system and storage solutions, customers are not automatically compliant with the standards. Most providers, including Atlantic.Net, offer customers multiple hosting options, some of which may not be concerned with the level of security and privacy demanded by HIPAA or PCI-DSS. These less secure systems would be used for personal websites for example or development work.
Make sure you fully understand the certification standing of the hosting package you select and verify that it meets your requirements. As a potential customer, you can have access to SOC 3 reports and certifications that demonstrate the provider’s ability to protect sensitive data.
 Third-party audits
Third-party audits
Providers should use third-party audits to verify to themselves and their customers that they are adhering to the audited standards. Self-assessments are a good place for organizations to start determining if they are compliant or if changes need to be made to reach that goal.
After addressing the issue found in a self-assessment, trained third-party auditors can ensure that standards are being met and supply HIPAA, HITECH, PCI-DSS, SOC 2, or SOC 3 certifications. Having a second set of eyes focused on compliance helps organizations avoid the pitfalls of non-compliance.
 Fines for noncompliance
Fines for noncompliance
Substantial fines can be levied against entities not conforming to the appropriate data handling guidelines. In the case of PCI-DSS, fines can range from $5,000 to $100,000 per month until the noncompliance issue is resolved.
HIPAA penalties are determined based on the scope and severity of the data breach. The most severe transgressions can cost an organization $1.5 million per year. There are also potential criminal penalties for using PHI maliciously that can lead to 10 years in prison.
 Why Choose Atlantic.Net?
Why Choose Atlantic.Net?
Contracting with Atlantic.Net for HIPAA-compliant hosting or PCI-DSS-compliant web hosting gives you peace of mind that your provider knows what they’re doing. Atlantic.Net is SOC 2, SOC 3, HIPAA audited, and PCI ready and provides customers in the healthcare industry and those who process credit cards with the hardened, secure, and compliant infrastructure they need. They enable clients to effectively maintain HIPAA and PCI-DSS compliance.
Learn more about our HIPAA compliant web hosting and HIPAA cloud hosting solutions.