Table of Contents
- How to Maintain HIPAA Compliance When Using Cloud Storage Services or File Sharing Services
- How Does HIPAA Affect Cloud Service Providers and Users?
- Penalties for Cloud Computing-Related HIPAA Violations
- HIPAA-Compliant File Sharing and HIPAA-Compliant Cloud Storage Services FAQs
- Your 10-Step HIPAA (Health Insurance Portability and Accountability Act) Checklist
How to Make Cloud Storage HIPAA Compliant?
HIPAA (the Health Insurance Portability and Accountability Act) compliance is all about protecting the integrity of Protected Health Information (PHI), and a major part of the Federal law requires a wide range of security and privacy safeguards to protect patient data at rest or in transit according to the HIPAA Privacy Rule and HIPAA Security Rule. What this means is that when your medical files are traveling around cyberspace, it must be done with the utmost due diligence in a cloud computing environment that is designed to protect against any form of a data breach and prevent an unauthorized user’s attempt to access files.
How can you take advantage of the incredible power of cloud hosting while still meeting HIPAA-compliant cloud storage requirements at all times?
The best way currently available to store your medical files and share them between various parties is with HIPAA-compliant hosting. Different cloud apps are designed for file-sharing (examples include Box, Dropbox, and Google Drive), allowing you to back up the files and synchronize data between various devices. However, general technological solutions are not designed for the particular case of healthcare concerning encryption of electronic protected health information, which is where HIPAA-compliant cloud storage services can help.
How to Maintain HIPAA Compliance When Using Cloud Storage Services or File Sharing Services
When a public cloud provider declares it is HIPAA compliant, this means the underlying infrastructure is secure. HIPAA-covered entities are still responsible for using identifying out-of-scope HIPAA requirements that the HIPAA-compliant cloud provider is not responsible for, monitoring for security incidents, and auditing their activity. Below are the key activities covered entities must carry out after they start using a HIPAA-compliant cloud storage service (or any HIPAA enterprise cloud services).
Sign a BAA (Business Associate Agreement) with Your Cloud Storage Service Provider
The first step to HIPAA compliance is to sign a Business Associate Agreement (BAA) with the cloud storage services provider. This should help establish the guidelines of the relationship between the two entities.
Establish a Responsibility Matrix for HIPAA Controls
Most providers will have a responsibility matrix ready to share to establish what the HIPAA cloud storage service provider will and will not be covered in terms of required HIPAA controls. Establishing which entity will be responsible for what is a key function to ensure nothing is missed when establishing HIPAA compliance.
Set Up Appropriate Access Controls
The cloud user must ensure that access controls are carefully configured so that only authorized individuals can access PHI. It is necessary to establish procedures for granting, revoking, and periodically reviewing access.
Set Up Patch Management
Ensure that all cloud systems are upgraded to the latest versions of their respective operating system and software. Put monitoring in place, ensure operations staff are notified when a patch is needed, and have a convenient way to apply patches to cloud systems.
Set Up Firewalls with Logging
HIPAA requires that local cloud storage data centers and workstations should be behind a firewall. HIPAA rules also require recording, auditing, and monitoring of any access to PHI data. This means that logging should be enabled on any firewall, whether deployed on-premises or in the cloud.
Set Up Controls for File Integrity Monitoring
The cloud user must set up measures that ensure PHI integrity. The organization should have a record of any unauthorized access to PHI and any changes made to the data and should be able to ensure any healthcare data is “authentic”.
Make Sure Encryption is in Place
End-to-end encryption is mandatory for any data transmitted to or stored in the cloud. Systems should be in place to coordinate encryption keys between on-premise and cloud storage services.
Set Up Appropriate Processes for a Breach Notification
When a data breach has occurred, both the cloud user (the covered entity) and the cloud provider (the business associate) should investigate and report their findings to the OCR.
Provide Training for Employees
Any employees who work with protected health information (PHI) or related systems must be aware of the relevant security procedures and what they are and are not allowed to do with the data. An ongoing training program is essential to ensuring HIPAA controls are enforced within the organization.
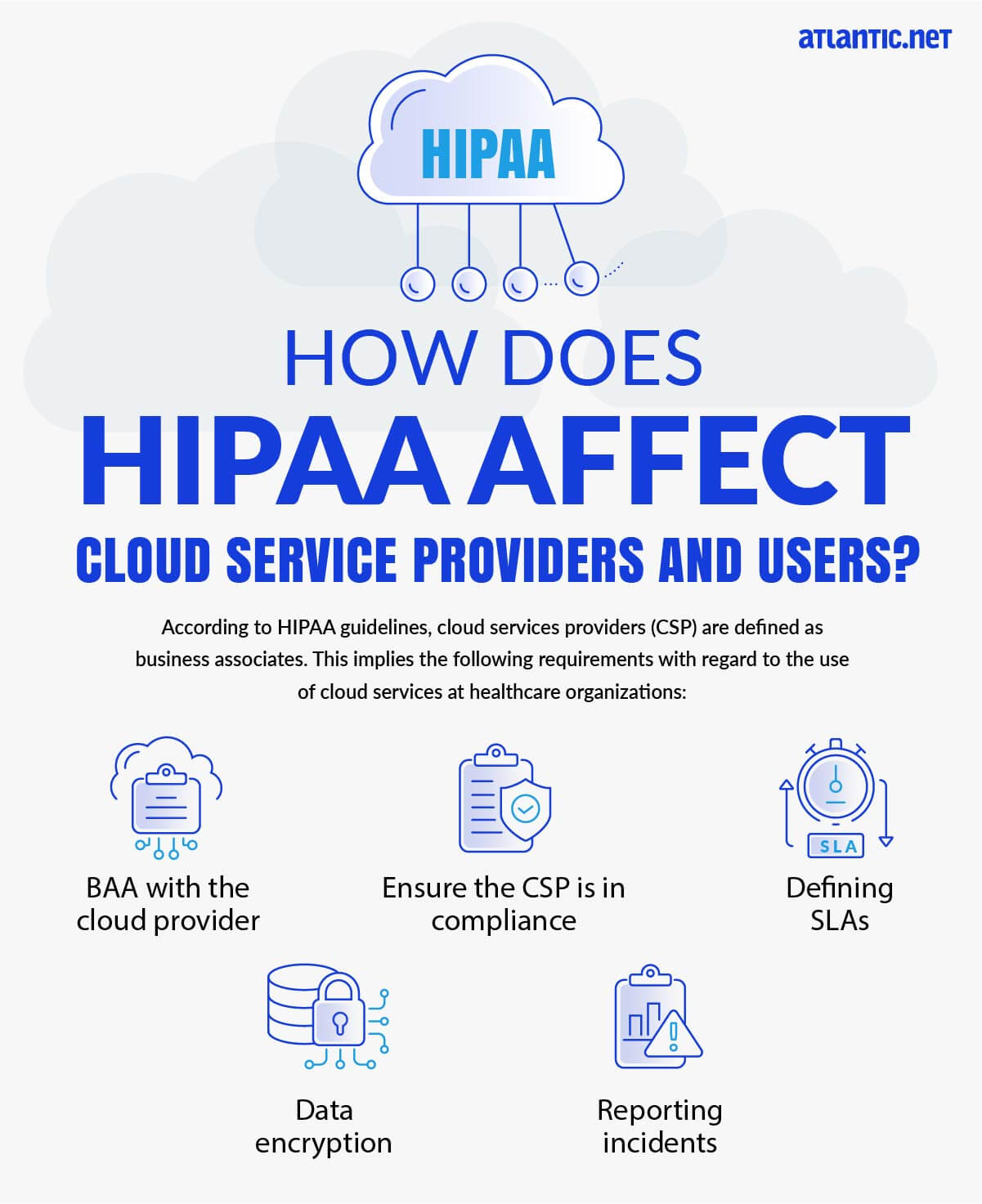
How Does HIPAA Affect Cloud Service Providers and Users?
According to HIPAA guidelines, cloud services providers (CSP) are defined as business associates. This implies the following requirements with regard to the use of cloud services like those of a cloud storage provider at healthcare organizations:
- BAA with the cloud provider—covered entities may use cloud services to store or process ePHI; however, they must enter a BAA with the cloud service provider.
- Ensure the CSP is in compliance—it is not enough to sign a BAA. Covered entities must make sure that the cloud provider complies with all relevant HIPAA regulations.
- Defining SLAs—covered entities need to receive a Service Level Agreement (SLA) commitment from their cloud providers which addresses HIPAA requirements like system reliability andavailability, data backup, data recovery, security responsibilities, retention of PHI, disclosure, and more.
- Data encryption—if the cloud provider stores encrypted PHI without an encryption key, they are still considered a “business associate” and are subject to the same responsibilities for securing the data.
- Reporting incidents—when a security incident happens, the cloud provider must report it to the covered entity (cloud user) as soon as the vendor discovers the incident. According to HIPAA, cloud providers are required to detect as well as respond to any security incident. The cloud vendor is also required to mitigate security threats as well as record the details of the incident and its consequences.
Penalties for Cloud Computing-Related HIPAA Violations
If an organization carries out HIPAA violations, the state Attorney General may impose fines of up to $25,000 per year per category of violation, and the Office for Civil Rights (OCR) can impose fines of up to $1.5 million per year per category of violation. Individuals who violate HIPAA can also face fines and criminal penalties of up to 10 years in prison. There were several cases tightly related to cloud services where HIPAA violations resulted in court settlements and large fines, including:
- Phoenix Cardiac Surgery—did not enter a business partner agreement with an Internet-based calendar and email service provider. PHI-related information was transmitted using the service.The organization settled its case with OCR for $100,000.
- University of Oregon Health and Science University—stored PHI in a cloud service without entering a BAA with the cloud provider. Settled the OCR lawsuit for $2.7 million.
- St. Elizabeth Medical Center in Brighton, MA—uploaded PHI to a cloud file-sharing service without assessing the risks and paid $218,000 in fines after a settlement with OCR.
HIPAA-Compliant File Sharing and HIPAA-Compliant Cloud Storage Services FAQs
Is Security Awareness Training Mandatory?
Yes, it is a mandatory requirement of HIPAA compliance for both covered entities, like healthcare providers, and their business associates to provide training to their employees about HIPAA compliance and the physical safeguards, administrative safeguards, and technical safeguards needed to protect patient data – including when using file-sharing services.
Your staff should know reasonable ways (as with phishing prevention) to guard against the intrusion of malware, and they should understand when it is appropriate and inappropriate to access health data, including as it relates to file-sharing solutions.
In order to prevent non-compliant password sharing, you want to have strong password policies implemented. An organizational culture that respects HIPAA compliance is founded on training that ensures your workforce has strong security knowledge and understands the physical, administrative, and technical safeguards employed to enforce data protection according to the Security Rule and Privacy Rule of HIPAA.
How Do I Protect PHI Data in Transit? Do I Need to Protect PHI on Mobile Devices, Too?
Preventing unauthorized access to Protected Health Information is of the utmost importance, whether the data is moving or at rest. When considering data-in-transit, protections are critical because mobile devices are increasingly used to send health data and health information exchanges (HIEs). There are two key elements to consider regarding data security in transit:
There are two key elements to consider:
- Protect data in transit using security protocols, best practices, and secured systems
- Encrypt all files in transit containing medical records/health data
To achieve this, each employee has the personal responsibility to consistently encrypt in-transit data, including when it is being sent using file-sharing services. It does not matter if your staff has no encryption expertise or background in data security; training must be provided. This training must explain the “dos and don’ts” when it comes to transmitting PHI and when it is not acceptable. A minimum of AES256 bit encryption must be used and PHI should not be sent via email unless encrypted first. As mobile tools and mobile platforms are more frequently used to share such sensitive patient information, sensitive files must be encrypted there, too. Covered entities must have policies in place to send a secure file with robust mobile security, including encryption of data in transit and controls on mobile access as with other workstations and devices.
How Do I Protect Employee Workstations?
Healthcare organizations must put policies and procedures in place that address how their employees can access and use end-user devices, typically smartphones, tablets, laptops, and workstations. Create policies and procedures that control how media is transferred, decommissioned, thrown out, or reused. All pertinent health data must be destroyed prior to any equipment reuse.Key concerns for this aspect of physical security are:
- the number of individuals who use the workstation; and
- whether it is in a private or public setting.
Why Do I Need a Security Management Plan?
In order for your staff to properly follow administrative safeguard rules, you will need policies and procedures to support a comprehensive security management approach. A critical aspect of this effort is a risk analysis and management process. Overall, this plan is based on the need to maintain the availability, integrity, and confidentiality of health data.
What Audit Controls are Needed to Protect PHI?
HIPAA compliance requires detailed logging of nearly all aspects of a system that hosts PHI. The logging and analysis of everything that occurs within these systems are essential.
Anyone handling health data, whether a covered entity or business associate, will want to assess what the intervals will be for auditing, the specific processes used to study the ePHI, the location of data for audit results, and the policy for personnel who do not follow guidelines.
Detailed logging to smart SIEM solutions can offload a large amount of the workload to AI, and combining intelligent monitoring, an intrusion protection service, and due diligence creates the best environment to protect and audit sensitive data.
How Do I Respond to a File Sharing Security Incident?
In order to comply with HIPAA, healthcare providers have to know how they will respond to security incidents in advance with documented policies and procedures. A key element is evaluating the spectrum of different incidents that could potentially occur when using HIPAA-compliant file-sharing services.
The procedures should specifically indicate an individual who is the organization-wide point-person to be notified if a security incident occurs (i.e., your HIPAA Security Officer, who may also be your HIPAA Privacy Officer).
Everyone who is working at your organization should know exactly what they need to do in various types of difficult scenarios in order to make sure digital health data is safe no matter the situation.
What Authentication Methods Should I Use?
You want robust and thorough steps in place to authenticate secure access to your systems and determine the real identities of all users – this applies to more than just HIPAA-compliant file sharing. One such method to achieve this is by using user accounts (such as Active Directory) that have minimum password requirements, lockout capabilities, unique user IDs, and are centrally managed, either in-house or by your MSP.
The budget should be considered alongside training and the actual procedures and protocols that will be utilized. Authentication is necessary so you can determine whether someone has the correct permissions for ePHI or what the source of transmission is. Multi-factor authentication provides the best possible protection to sensitive healthcare data for HIPAA compliance. MFA and two-factor authentication are widely used, and just like it does with mobile banking, MFA will protect access to your secure file transfer accounts. The same principle applies to PHI in a HIPAA-compliant context; MFA helps greatly in protecting PHI when using a secure file transfer tool for HIPAA-compliant file sharing.
Who Protects Facility Access Controls?
Any facility where HIPAA-compliant file sharing is performed as part of procedures will also need to abide by HIPAA guidelines on access controls.
Separate from the question of HIPAA-compliant file sharing, a facility that is subject to HIPAA regulation can be any physical location that is used to house PHI; this may be a terminal in a hospital, the data centers of your managed services provider, or an employee cell phone. You need to go above and beyond protecting your workstations and devices, all the way to considering the whole building. Do you require a 24×7 security guard presence, CCTV monitoring, and potentially even further physical security measures in the facility?
Ensure your security measures restrict physical access to people without proper authorization. While all of the stipulations for access controls – maintenance records, access validation and control procedures, contingency operations, and a facility security plan – are “addressable” rather than “required,” you still must use any of these elements that you find are appropriate based on analysis of your situation.
What Integrity Controls are Needed?
From an administrative perspective, ensuring the integrity of your data (verifying that it is not wrongly destroyed or changed) requires you to establish (via policies and procedures) rules against wrongfully destroying or changing health data.
Consider how to promote data integrity when information is at rest (stored) and in-motion (transmitting). Malicious individuals could threaten the smooth operation of your organization and potentially do severe damage to your finances and reputation. You want to know the extent to which your data’s integrity is protected against manipulation.
Notably, you can best protect your critical information through authentication as achieved via checksum technology, digital signatures, magnetic disks, and error-correcting memory.
Any analysis of threats to integrity should include a look at outside individuals as well as people who are legitimately working for you but are error-prone or who may become disgruntled.
How Do I Control Access to PHI Data?
One of the greatest fundamentals of security is to only give information to the people who are supposed to be able to see it, blocking access to others. A HIPAA-compliant organization must assess the procedures they have deployed (including any that rely on HIPAA file sharing) and add defenses so that they can mitigate inappropriate ePHI access and disclosure of sensitive files.Information access is based on a need-to-know basis: make sure your management plan complies with the minimum necessary stipulations in the HIPAA Privacy Rule.
Which File Transfer Programs are HIPAA-Compliant?
It is not necessarily the program that must be HIPAA-Compliant; rather, it’s critical that the environment where the program is used is abundantly secure. When dealing with PHI, companies must make sure that they are using a HIPAA-compliant file transfer platform to protect the integrity of sensitive data.
HIPAA legislation requires organizations to implement the following to ensure compliance:
- Access control
- Data encryption
- Audit logging
- User authentication
- Data backups and disaster recovery
- Business Associate Agreements (BAA)
What is a HIPAA-Compliant Business Associate?
HIPAA compliance goes beyond the above file transfer and HIPAA-compliant cloud storage methods to encompass consideration of your entire ecosystem, including sometimes trusting third parties (business associates) to strengthen your approach. Do you represent a HIPAA-covered entity looking for HIPAA-compliant web hosting for your online healthcare presence, or do you need HIPAA-compliant cloud storage services for your practice or healthcare organization? At Atlantic.Net, over the years, we’ve steadily built a reputation as an exceptional healthcare HIPAA storage company, known for demonstrating trustworthiness to our healthcare industry clients and offering a Business Associate Agreement as part of our commitment to maintaining HIPAA compliance for healthcare providers and healthcare organizations who need help protecting PHI.
Get Help with HIPAA Compliance
Atlantic.Net stands ready to help you attain fast compliance with a range of certifications, such as SOC 2 and SOC 3, HIPAA, and HITECH, all with 24x7x365 support, monitoring, and world-class data center infrastructure. For faster application deployment, HIPAA web hosting, HIPAA-compliant cloud storage services, free IT architecture design, and assessment, call 888-618-DATA (3282), or contact our sales team at [email protected].
Your 10-Step HIPAA (Health Insurance Portability and Accountability Act) Checklist
Read More About HIPAA Compliance
- HIPAA Compliance Checklist
- How to Become HIPAA Compliant
- What Is the HIPAA Security Rule?
- Top Considerations for HIPAA File Storage
- Protecting e-PHI in the Cloud
- What Is HIPAA Cloud Computing?
- What Is Healthcare Hosting?
- What Is PHI?