Table of Contents
- What Is Protected Health Information (PHI/ePHI)?
- Who Interacts with ePHI?
- Why Is Protected Health Information (PHI/ePHI) So Important?
- How Does the Security Rule Protect PHI / e-PHI?
- How Do You Protect PHI in the Cloud?
- How Do I Make My Cloud HIPAA Compliant?
- What Happens If You Don't Protect PHI Data?
- Can HIPAA Data Be Stored in the Cloud?
- How Do I Make My Cloud HIPAA Compliant?
- Atlantic.Net HIPAA-Compliant Hosting
What Is Protected Health Information (PHI/ePHI)?
Protected Health Information (PHI) is any personally identifiable patient data that specifically relates to a patient. This might be data written to medical files, patient reports, diagnosis data, medical insurance data, and so on. In most circumstances, ePHI is actually electronic protected health information (ePHI) as it is stored on data storage in a digital format, often using a HIPAA cloud service provider (CSP) who is a business associate of the organization.
HIPAA, the Health Insurance Portability and Accountability Act, was signed into law in 1996. There were two main objectives of the new legislation. The first was to enable Americans to move their health insurance between jobs; this was a clear-cut goal that was achieved almost overnight.
The second was to enforce privacy over health information. This is what most healthcare organizations and covered entity professionals are concerned with when referring to HIPAA compliance – the “Accountability” portion of HIPAA – because it was created to maintain the privacy and security safeguards of US patients’ PHI.
Who Interacts with ePHI?
Healthcare providers and any business associate who works with them, such as a cloud service provider (CSP), will typically interact with Protected Health Information (PHI) every day. PHI may be located on mobile devices, hospital technologies such as CT scanner equipment, and so forth, resulting in potentially huge volumes of patient data becoming available.
HIPAA demands security awareness by all staff of a covered entity or business associate. Health records are expected to have data encryption security standards in place, and risk analysis will ensure that the healthcare organization or covered entity knows exactly what PHI they have and if it meets the required compliance requirements.
If there are issues, security controls must be in place to protect against data breach incidents. Data security is essential, and any data breach incidents must be reported to the HSS Office for Civil Rights, per the breach notification rule.
Why Is Protected Health Information (PHI/ePHI) So Important?
PHI data protection is crucial to HIPAA compliance, and a covered entity must understand what constitutes PHI. A covered entity is anyone who is involved in the treatment and day-to-day operations of a healthcare provider.
Covered entities are typically healthcare organizations, healthcare clearinghouses (for health plans), healthcare insurance companies, or entities that create patient data ready for data storage.
Here are some popular examples of what constitutes PHI. Each example falls under the data protection requirements of the Privacy Rule, and the confidentiality, integrity, and availability of the Security Rule, and must be upheld by all business associates:
- Treatment reports
- Lab results
- Test results
- Prescription information
- Any information that includes the name
- Phone numbers
- Address
- Social security number
- Medical records number
- IP address
- Health insurance details
It is easy to see how such large volumes of PHI can be created, and it’s easy to see how a healthcare provider can get bogged down with so much patient data. HIPAA was created to introduce data protection, security controls, and access controls to all of this data.
How Does the Security Rule Protect PHI / e-PHI?
The clue is in the title. The HIPAA Security Rule defines the three main standards or blueprints of how to protect PHI / ePHI data. Adhering to these safeguards is the most effective way for a covered entity and business associate to become HIPAA compliant.
The 3 safeguards are:
- Physical Safeguards for ePHI
- Technical Safeguards for ePHI
- Administrative Safeguards for ePHI
All physical precautions refer to the implementation specifications for real-life physical controls on digital devices that store and handle ePHI data. Some of the key areas for consideration are how old or faulty equipment is replaced – for example, how ePHI media and electronic protected health information (ePHI) data is destroyed once it has served its purpose.
Another consideration is what personnel access levels are granted and put in place to in-scope systems containing ePHI; specifically, covered entity / covered entities must ensure that access is only granted to employees with a relevant level of authorization and how to train 3rd-party IT professionals when accessing the in-scope equipment for repairs.
The technical assurances of the HIPAA Security Rule are more easily defined and include the technical aspects of any networked computers, storage media, or devices that communicate with each other and contain PHI in their transmissions.
These precautions include enhanced network security, perimeter firewalls, cybersecurity authentication protocols, and more. Any security measures that can be implemented on system software or hardware belonging to the HIPAA security rule’s technical protection category.
The administrative guarantees cover how the covered entity / covered entities must set up their employee policies and procedures to comply with HIPAA’s Security Rule. Think of it as a separate, dedicated portion of employee training, both for management and staff, that defines who gets access and what they can and cannot do once access is granted.
The Security Rule breaks down these safeguards into two groupings: required and addressable. Put simply, a required standard applies to everyone, and addressable is if appropriate. If an addressable standard is not appropriate, there must be documentation explaining why,” explains the HIPAA compliance auditors at I.S. Partners.
How Do You Protect PHI in the Cloud?
Cloud computing is a rapidly expanding industry, and the number of organizations adopting virtualized environments provided by a CSP in the cloud continues to grow across all industries, including the healthcare industry. Traditionally, a US healthcare provider has been considered slow to adapt and engage new models of service such as those offered by a CSP, often held back by bureaucracy. These stereotypes are definitely starting to change, with many cloud services providers (CSP) recording record uptake from numerous US healthcare providers.
There are several CSP options out there, but only Atlantic.Net specializes in HIPAA-compliant server hosting that meets and exceeds the requirements of HIPAA, the Privacy Rule, and the Security Rule. Atlantic.Net knows that one size does NOT fit all, so unlike the hyper-scale cloud service provider (CSP), Atlantic.Net’s unique turnkey solutions will work exactly for your needs!
Cloud providers enable flexibility that most healthcare organizations or covered entities will benefit from, but many are held back by a lack of clarity about what the cloud is, and how it relates to the HIPAA web hosting and PHI. A cloud service provider (CSP) will supply the IT systems you need to meet compliance.
Get a Business Associate Agreement (BAA) with Your CSP
It starts by getting a signed business associate agreement, or BAA. A business associate agreement ensures that the covered entity, such as the healthcare providers, are legally protected, and that the cloud provider and all other business associates, such as subcontractors, guarantee that the services offered under the BAA uphold confidentiality, integrity, and availability of ePHI. Remember, managing PHI correctly will provide the best possible protection against healthcare data breaches, so having a service level agreement locked in on a business associate agreement (BAA) should be one of the very first things to do with the cloud provider (CSP).
How Do I Make My Cloud HIPAA Compliant?
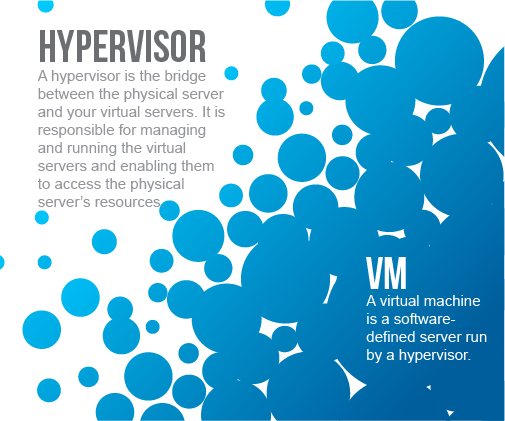
First, you need to understand what a HIPAA cloud is. It is a collection of server infrastructure and data storage with a secured network interlink. Each physical server runs a complex piece of software called a Hypervisor, and it’s the Hypervisor that splits up system resources that are allocated to your Virtual Environment.
Proprietary cloud software is used to create a front-end control panel that provides a user-friendly interaction with cloud resources. However, in the background, system engineers and security experts at the CSP are keeping the entire platform safe and 100% operational, and it’s the cloud control panel that interacts with all of these resources.
Behind the scenes, the HIPAA-compliant cloud provider must ensure that the platform adheres to the stringent requirements for each of the Administrative, Physical and Technical safeguards of HIPAA. This is not an easy task, which is why so many healthcare providers choose to outsource this responsibility to a CSP business associate.
What Happens If You Don’t Protect PHI Data?
HIPAA compliance can be particularly scary for organizations due to the worry and implications of facing a data breach, the complexity of the regulations, and the severity of potential fines.
Timely access to medical information can be a matter of life and death, but ensuring that information is accessible, portable, and renewable only covers Title I of the Act. Title II, covering health care fraud and abuse, along with the enforcement-strengthening HITECH Act, imposes data security and privacy rules on health care providers and any business associate that supports them, such as a CSP (get that business associate agreement (BAA) signed and put in place).
PHI Compliance Failures
Compliance failures can result in fines of up to $1.5 million, and data breaches, which are increasingly common in healthcare, can be even more expensive, particularly when reputational harm is considered. Did you know that if your PHI / ePHI is breached, and more than 500 records are at risk, the breach notification rule requires that the media is notified? It’s clear to see the impact this will have on a covered entity, not to mention the patient!
Fortunately, virtualized cloud environments can not only be HIPAA-compliant quickly with the help of a CSP but also can make compliance easier.
Can HIPAA Data Be Stored in the Cloud?
The Technical Safeguards set out in the HIPAA Security Rule of 2003 layout the technicalities of what is needed and include the technical aspects of any networked computers or devices that communicate with each other and contain PHI / ePHI in their transmissions.
These safeguards include enhanced network security, enhanced system security, anti-malware, perimeter firewalls, data availability, cybersecurity authentication protocols, and more; essentially, any security rules or measures that can be implemented on system software or hardware belonging to the HIPAA security rule technical safeguards category. Your business associates will typically manage this, but the requirements of data security are a shared responsibility between the covered entity and the cloud providers.
How Do I Make My Cloud HIPAA Compliant?
Let’s dig into the technology available from a cloud provider business associate like Atlantic.Net. The technology stack of each cloud provider will vary, but each will use virtualization. There are different kinds of hypervisors offered by a CSP, and the most appropriate for any given healthcare organization depends on the healthcare providers’ needs and other information technology tools currently in use.
What should be common to each one is that the isolation and abstraction of the virtual machines (VMs) they create give them robust access, security, and privacy compliance capabilities. Each VM set up by the hypervisor is self-contained and keeps its data isolated from any other VMs and their data. Ensure to ask your business associate/CSP if this is how they have their cloud environment set up since some older types will share kernels and other parts of systems.
This enables even VMs with different operating systems to run simultaneously on the same hardware. The separation the hypervisor provided between the instance and the physical server makes the information system “agile.”
It allows virtualized servers to be moved, for example, in the case of a hardware failure, which keeps whatever function is being “served” working. The hypervisor also manages the hardware resources available to it to run an organization’s VMs as efficiently as possible and to provide the ability to scale to maintain availability when demand on the network is high. It also enables data backup and data recovery possible at scale.
Virtualization and Compliance
There are three hypervisors available to Atlantic.Net HIPAA cloud services customers: Proxmox, Hyper-V, and Cloud.
Proxmox
An open-source alternative based on the Linux Kernel Virtual Machine (KVM), Proxmox is managed with a web graphical user interface (GUI) and is known for solid performance and flexibility.
It works reliably with different operating systems but also supports different storage options, including Linux containers. Any storage type used can be accessed only through the hypervisor layer, allowing access restrictions compliant with HIPAA’s Title II and HITECH rules.
When set up in a server cluster or utilizing “shared” cloud storage, Proxmox allows live migration of running machines. This makes the system agile enough that maintenance or updates necessary to keep the virtual server compliant from a security perspective can be performed without downtime, preserving compliance with the availability rules of HIPAA’s Title I.
First released publicly in 2008, Proxmox is updated about every six months. It is built to work flexibly with a variety of different products, rather than those from a particular company like Microsoft as is the case with Hyper-V, which could make Proxmox a better fit for some organizations.
Proxmox sometimes requires CSP support teams to use the command line, which for some, may not be ideal. However, Atlantic.Net has around-the-clock technical support available from a team of specially trained cloud technology engineers, available 24x7x365.
Hyper-V
Microsoft’s Hyper-V is designed for Windows servers and desktops, making it a popular choice for organizations that predominantly use the Windows ecosystem. Unlike Proxmox, Hyper-V is a closed-source software solution.
However, the separation and control of access through the hypervisor layer are very similar, as is support for live migration. Hyper-V keeps data in a securely isolated environment to maintain compliance with rules for fraud, abuse, and privacy while also enabling the constant access and portability HIPAA compliant cloud computing requires.
Hyper-V includes “dynamic memory management,” a feature making it easy to scale up the number of cloud virtual machines in use. It also features Windows Active Directory for security and access management, perfect if you are already using Active Directory.
Organizations considering Hyper-V should be aware that it tends to work best with the latest version of Windows, though it also works with other operating systems, including Linux and FreeBSD. Hyper-V was originally launched with Windows Server 2008, and Microsoft maintains it with frequent updates.
Cloud
Atlantic.Net’s HIPAA Cloud environment is based on KVM, much like Proxmox. Therefore, data is isolated in the same way, on an abstracted hardware layer available only via the hypervisor.
Cloud environments allow customers fine-grained control to pay only for the resources they use and scale up those resources to meet demand increases. It is, therefore, an efficient and economical solution for organizations with high variations in IT workload. Atlantic.Net launched its first cloud servers in 2010 and has been steadily expanding its CSP offerings since.
Software Secures Borders, Physical or Virtual
Just as the software borders between VMs are like the hardware boundaries between physical machines, the tools that secure a network against malicious traffic are similar. Traffic should be controlled with a firewall, all the elements of the site should be secured with two-factor authentication, and off-site data backups must be maintained to meet the Title I standard of accessibility.
Those and all of the other necessary features and technologies for HIPAA compliance in a server can be met with the appropriate implementation of any cloud virtual environment from Atlantic.Net, your business associate.
Regularly scheduled, automated backups are available with all Atlantic.Net virtualized HIPAA cloud environments, making continuous compliance not only possible but easier. Healthcare organizations can also provide auditors with automatically generated log information of network traffic created by either KVM or Hyper-V or a managed firewall with intrusion prevention, easily demonstrating the security and privacy necessary for Title II and HITECH compliance in HIPAA compliant cloud computing.
Every healthcare organization needs to follow privacy, security, and compliance best practices and partner with an IT provider business associate (with a BAA) they can trust to deliver compliant services, regardless of the network environment. Fortunately, this means flexibility, logging, automated backups, and other features of virtualized environments are an option for all.
How Do You Protect PHI?
While HIPAA regulations are complex and detailed, they contain little information on how to adequately protect PHI. So, what can you do to protect the integrity of your PHI?
- Produce formal documented policy and procedures for PHI use, disclosure, and disposal.
- Train employees in ePHI handling
- Implement encryption and remote wipe capabilities
- Utilize multi-factor authentication and a least-privileged approach
- Monitor and regularly audit the organization’s handling of ePHI
Atlantic.Net HIPAA-Compliant Hosting
In summary, if your organization has avoided or delayed moving HIPAA workloads to a virtualized environment out of compliance concerns, it is likely worth reconsidering the option. Atlantic.Net is committed to helping you protect your ePHI and ePHI data, and we also sign a Business Associate Agreement (BAA). Whether you are a covered entity, a healthcare provider that needs assistance with securing their data, as a CSP Atlantic.Net has you covered. Contact our knowledgeable sales team today by phone at 1-888-618-DATA (3282) or email [email protected] for information about HIPAA cloud hosting & storage services (including our HIPAA Cloud and Managed Cloud Solutions) and our BAA offering today!
Read More About HIPAA Compliance
- HIPAA Compliance Checklist
- How to Become HIPAA Compliant
- What Is the HIPAA Security Rule?
- Top Considerations for HIPAA File Storage
- HIPAA Data Storage Requirements
- What Is HIPAA Cloud Computing?
- What Is Healthcare Hosting?
- What Is PHI?