How to Setup Kerberos Server and Client on Ubuntu
November 28, 2023 by Hitesh Jethva ( 680 ) under Dedicated Server Hosting
0 Comments
Kerberos is a network authentication protocol that provides authentication against the devices to enable secure communication between client and server. It uses secret-key cryptography for verifying users’ identities. Generally, Kerberos is used in POSIX authentication, Active Directory, NFS, and Samba.
This tutorial will show you how to install the Kerberos server and client on Ubuntu. This procedure is compatible with Ubuntu 20.04 and Ubuntu 22.04.
Prerequisites
- Two fresh Ubuntu 20.04 VPSes on the Atlantic.Net Cloud Platform
- A root password configured on your server
In This Article
- Setup Hostname Resolution
- Install Kerberos Server
- Configure Kerberos Server
- Install Kerberos Client
- Verify Authentication
Step 1 – Setup Hostname Resolution
First, you must set up a fully qualified hostname on the server and client machine.
On the server machine, set the fully qualified hostname with the following command:
hostnamectl set-hostname server.myexample.com
On the client machine, set the fully qualified hostname with the following command:
hostnamectl set-hostname client.myexample.com
Next, edit the /etc/hosts files on both server and client machines and set up the hostname resolution so both systems can communicate using the hostname.
nano /etc/hosts
Add the following lines:
your-server-ip server.myexample.com your-client-ip client.myexample.com
Save and close the file when you are finished.
Step 2 – Install Kerberos Server
Next, you must install the Kerberos server package on the server machine. You can install all the packages with the following command:
apt-get install krb5-kdc krb5-admin-server krb5-config -y
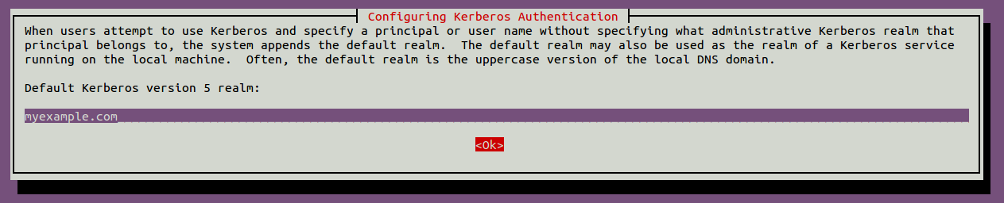
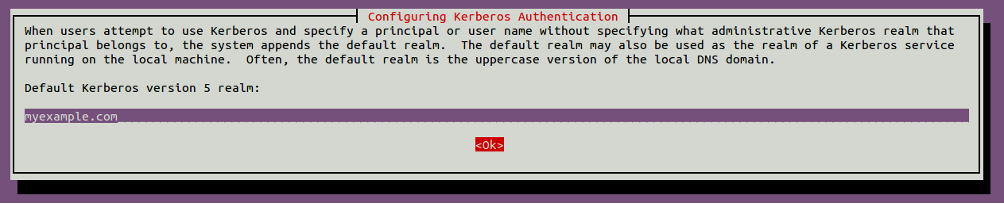
During the installation, you will be asked to provide Kerberos Realm, as shown below:
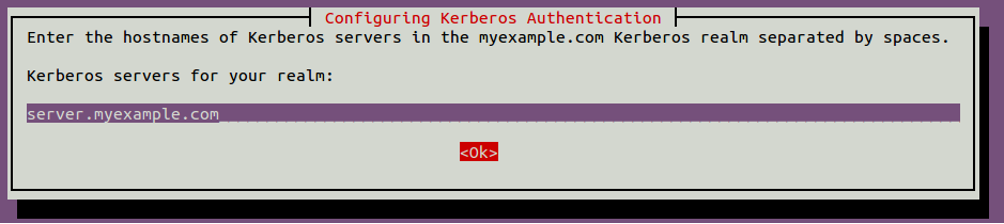
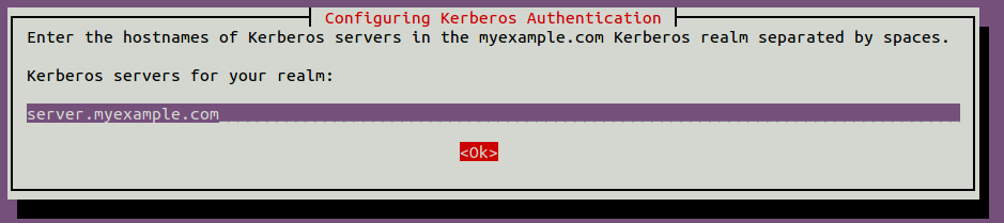
Provide myexample.com and click on the OK button. You will be asked to provide the Kerberos server hostname as shown below:
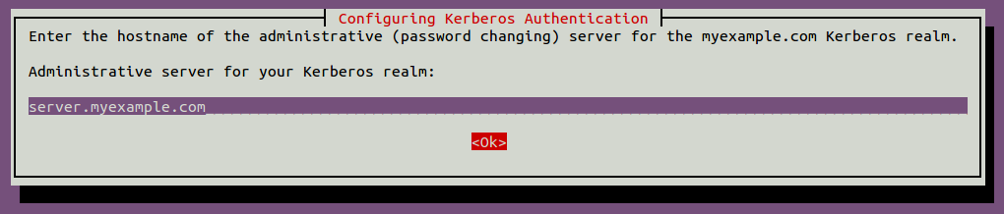
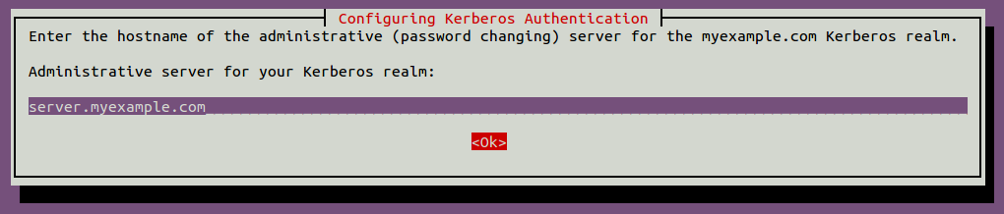
Provide server.myexample.com and click on the OK button. You will be asked to provide the hostname of the administrative server as shown below:
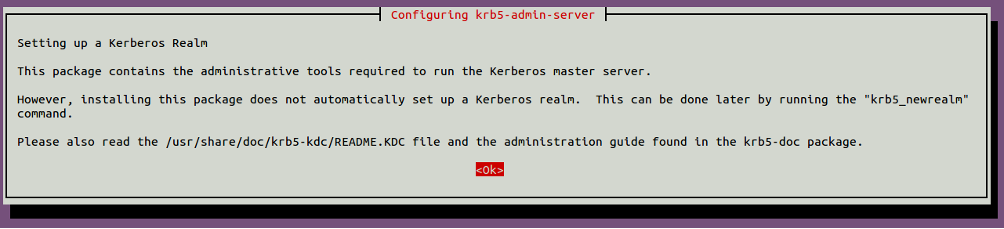
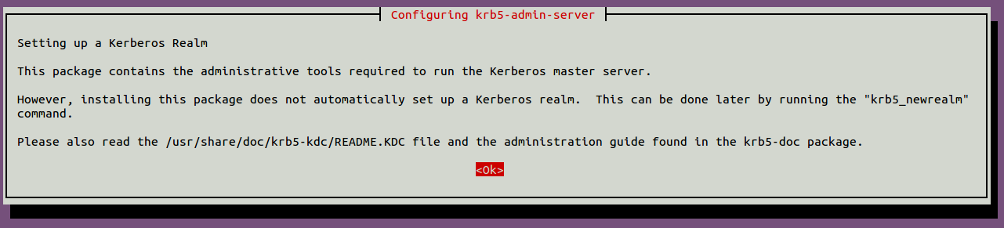
Provide server.myexample.com and click on the OK button. You should see the following page:
Click on the OK button to finish the installation.
Step 3 – Configure Kerberos Server
Next, you will need to generate the password for the Kerberos Realm. You can generate it with the following command:
krb5_newrealm
You will be asked to provide a secure password as shown below:
This script should be run on the master KDC/admin server to initialize a Kerberos realm. It will ask you to type in a master key password. This password will be used to generate a key that is stored in /etc/krb5kdc/stash. You should try to remember this password, but it is much more important that it be a strong password than that it be remembered. However, if you lose the password and /etc/krb5kdc/stash, you cannot decrypt your Kerberos database. Loading random data Initializing database '/var/lib/krb5kdc/principal' for realm 'myexample.com', master key name 'K/[email protected]' You will be prompted for the database Master Password. It is important that you NOT FORGET this password. Enter KDC database master key: Re-enter KDC database master key to verify: Now that your realm is set up you may wish to create an administrative principal using the addprinc subcommand of the kadmin.local program. Then, this principal can be added to /etc/krb5kdc/kadm5.acl so that you can use the kadmin program on other computers. Kerberos admin principals usually belong to a single user and end in /admin. For example, if jruser is a Kerberos administrator, then in addition to the normal jruser principal, a jruser/admin principal should be created. Don't forget to set up DNS information so your clients can find your KDC and admin servers. Doing so is documented in the administration guide.
Next, you must add the admin user principle to the access control. You can do it by editing the following file:
nano /etc/krb5kdc/kadm5.acl
Add the following line:
*/admin *
Save and close the file when you are finished.
Next, you must add the admin principal to the Kerberos database. You can do it with the following command:
kadmin.local
You should see the following output:
Authenticating as principal root/[email protected] with password.
Next, run the following command to add the principal name kuser:
kadmin.local: addprinc kuser
You will be asked to set the password as shown below:
WARNING: no policy specified for [email protected]; defaulting to no policy Enter password for principal "[email protected]": Re-enter password for principal "[email protected]": Principal "[email protected]" created.
Next, exit from the kadmin console with the following command:
kadmin.local: quit
Next, restart the Kerberos server with the following command:
systemctl restart krb5-admin-server
You can verify the status of Kerberos with the following command:
systemctl status krb5-admin-server
You should get the following output:
-
krb5-admin-server.service - Kerberos 5 Admin Server Loaded: loaded (/lib/systemd/system/krb5-admin-server.service; enabled; vendor preset: enabled) Active: active (running) since Sat 2020-11-07 06:22:19 UTC; 6s ago Main PID: 2183 (kadmind) Tasks: 1 (limit: 4691) Memory: 728.0K CGroup: /system.slice/krb5-admin-server.service └─2183 /usr/sbin/kadmind -nofork
Nov 07 06:22:19 server.myexample.com kadmind[2183]: Setting up TCP socket for address 0.0.0.0.464 Nov 07 06:22:19 server.myexample.com kadmind[2183]: Setting up TCP socket for address ::.464 Nov 07 06:22:19 server.myexample.com kadmind[2183]: setsockopt(12,IPV6_V6ONLY,1) worked Nov 07 06:22:19 server.myexample.com kadmind[2183]: Setting up RPC socket for address 0.0.0.0.749 Nov 07 06:22:19 server.myexample.com kadmind[2183]: Setting up RPC socket for address ::.749 Nov 07 06:22:19 server.myexample.com kadmind[2183]: setsockopt(14,IPV6_V6ONLY,1) worked Nov 07 06:22:19 server.myexample.com kadmind[2183]: set up 6 sockets Nov 07 06:22:19 server.myexample.com kadmind[2183]: Seeding random number generator Nov 07 06:22:19 server.myexample.com kadmind[2183]: starting Nov 07 06:22:19 server.myexample.com kadmind[2183]: kadmind: starting...
Step 4 – Install Kerberos Client
Next, you must install the Kerberos client on the client machine. You can install it with the following command:
apt-get install krb5-user -y
During the installation, you will be asked to provide Kerberos Realm as shown below:
Provide myexample.com and click on the OK button. You will be asked to provide the Kerberos server hostname as shown below:
Provide server.myexample.com and click on the OK button. You will be asked to provide the hostname of the administrative as shown below:
Provide server.myexample.com and click on the OK button. You should see the following page:
Click on the OK button to finish the installation.
Next, authenticate to the Kerberos server and obtain a ticket from it with the following command:
kinit kuser
You will be asked to provide a password for the kuser principal as shown below:
Password for [email protected]:
Next, obtain a ticket with the following command:
klist
You should get the following output:
Ticket cache: FILE:/tmp/krb5cc_0 Default principal: [email protected] Valid starting Expires Service principal 11/07/2020 06:25:40 11/07/2020 16:25:40 krbtgt/[email protected] renew until 11/08/2020 06:25:33
Step 5 – Verify Authentication
Next, you will need to verify the details of the principal on the Kerberos server.
On the Kerberos server machine, run the following command:
kadmin.local
Authenticating as principal root/[email protected] with password.
Next, print the principal details with the following command:
kadmin.local: getprinc kuser
You should get the following output:
Principal: [email protected] Expiration date: [never] Last password change: Sat Nov 07 06:21:46 UTC 2020 Password expiration date: [never] Maximum ticket life: 0 days 10:00:00 Maximum renewable life: 7 days 00:00:00 Last modified: Sat Nov 07 06:21:46 UTC 2020 (root/[email protected]) Last successful authentication: Sat Nov 07 06:25:40 UTC 2020 Last failed authentication: [never] Failed password attempts: 0 Number of keys: 2 Key: vno 1, aes256-cts-hmac-sha1-96 Key: vno 1, aes128-cts-hmac-sha1-96 MKey: vno 1 Attributes: REQUIRES_PRE_AUTH Policy: [none] kadmin.local: quit
Conclusion
Congratulations! You have successfully installed and configured the Kerberos server and client on Ubuntu 20.04. You can now use Kerberos on your network for the authentication of users. Try it on your dedicated server hosting account from Atlantic.Net!
Learn more about our dedicated servers.
Get a $250 Credit and Access to Our Free Tier!
Free Tier includes:
G3.2GB Cloud VPS a Free to Use for One Year
50 GB of Block Storage Free to Use for One Year
50 GB of Snapshots Free to Use for One Year