What Is HIPAA Compliance? HIPAA Compliance Checklist & Guide 2024
December 21, 2020 by Alexander Wise ( 29 ) under HIPAA Compliant Hosting
0 Comments
HIPAA compliance means meeting the requirements of HIPAA (the Health Insurance Portability and Accountability Act) and is regulated by the US Department of Health and Human Services (HHS). To help you understand the core concepts of compliance, we have created this guide as an introductory reference on the concepts of HIPAA compliance and HIPAA compliant web hosting.
In our 2024 HIPAA compliance checklist, we will illustrate the rule changes that have been introduced over the last 30 years. This post will serve as a detailed but easy-to-understand HIPAA compliance guide and will include everything you need to know about HIPAA. Next, we will offer our top tips to becoming compliant, with a PDF checklist for you to download, share, print, and keep.
This is part of an extensive series of guides about compliance management.
What is HIPAA Compliance?
HIPAA compliance is adherence to the physical, administrative, and technical safeguards outlined in HIPAA, which covered entities and business associates must uphold to protect the integrity of Protected Health Information (PHI).
How Do You Become HIPAA compliant?
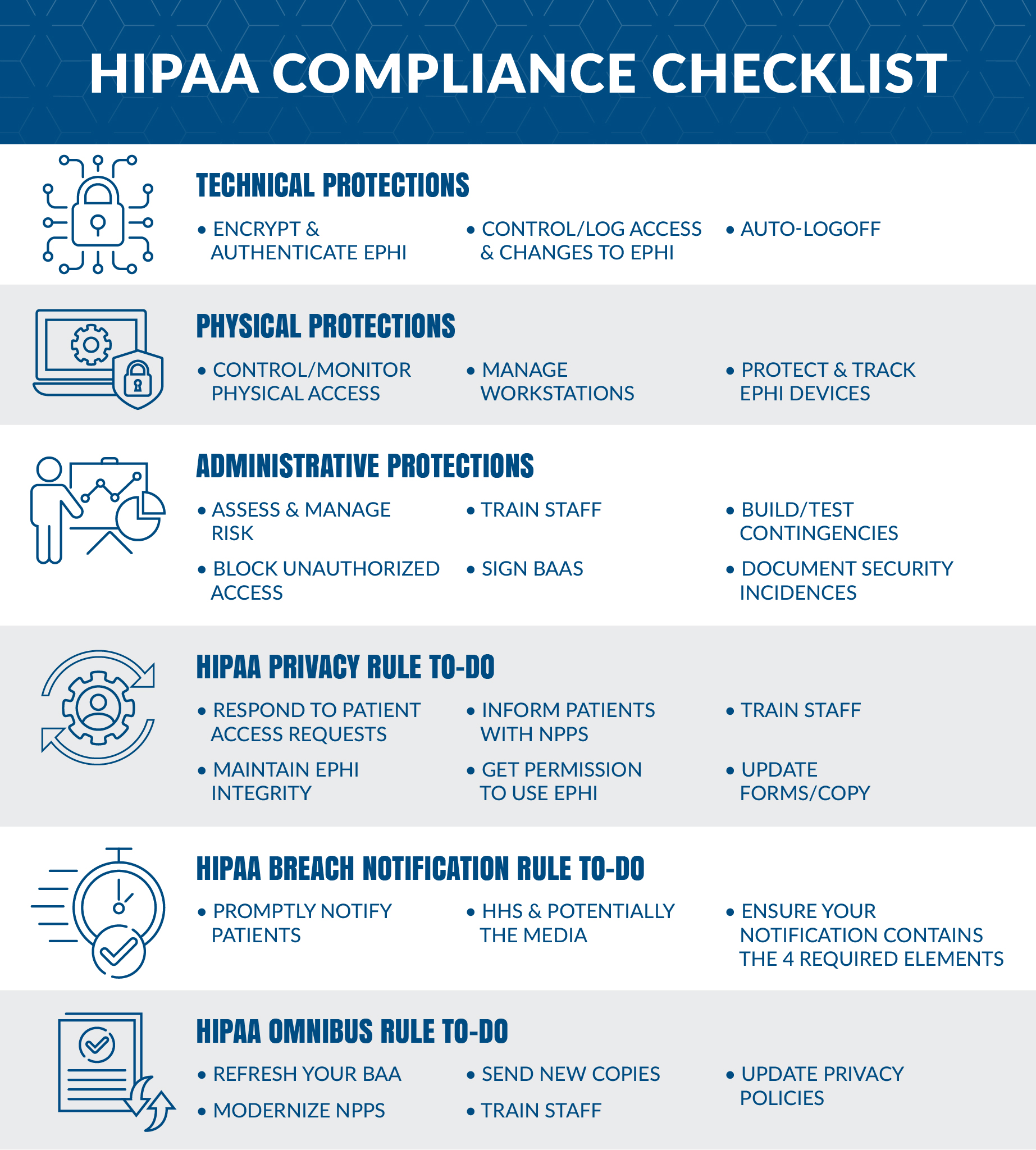
We have created this HIPAA compliance checklist to summarize what exactly is needed to become compliant. This checklist will include everything you need to know from the Security, Privacy, Breach Notification, and the Final Omnibus rules.
If you’re looking for assistance with HIPAA-compliant IT infrastructure, Atlantic.Net is at the forefront of HIPAA-compliant server hosting. With over 30 years of computing and networking experience, we offer world-class infrastructure and award-winning service, backed by US-based always available support. Visit our HIPAA-Compliant Hosting page for more information.
HIPAA Compliance 2024 Checklist Summary
In part 1 of this guide, we will summarise exactly what must be achieved to become compliant. HIPAA is quickly approaching its 25th anniversary, and the needs and demands of the legislation have changed as technology has advanced.
There have been four major amendments since 1996:
- The Security Rule Amendment of 2003
- Technical Safeguards
- Physical Safeguards
- Administrative Safeguards
- The Privacy Rule Amendment of 2003
- The Breach Notification Rule of 2009
- The Final Omnibus Rule of 2013
HIPAA Security Rule
The HIPAA Security Rule outlines the requirements for the protection of electronic patient health information. The Security Rule refers to “Security Standards for the Protection of Electronic Protected Health Information.”
What technical safeguards are needed?
- Network encryption – Encrypt any ePHI to meet NIST cryptographic standards any time it is transmitted over an external network. (Mandatory)
- Control access – Each user is assigned a centrally-controlled unique username and PIN code to access the systems. Procedures must also be in place to govern when to release or disclose ePHI during an emergency. (Mandatory)
- Authenticate ePHI – You must identify and authenticate ePHI and protect it from corruption, unauthorized changes, and accidental destruction. (Recommended)
- Encrypt devices – All end-point devices that access the system should be able to encrypt and decrypt data, this is particularly important for mobile and laptop devices. (Recommended)
- Control activity audits – Detailed logging is needed to track all ePHI access attempts and to monitor how ePHI data is manipulated. (Recommended)
- Enable automatic logoff – Users must be logged out after a certain set time frame, usually between 30 seconds and 3 minutes depending on the application or system (Recommended)
What physical safeguards are needed?
- Control facility access – You want to carefully track the specific individuals who have physical access to data storage – not just engineers, but also repair people and even custodians. You must also take reasonable steps to block unauthorized entry. (Required)
- Manage workstations – Write a policy that limits which workstations can access health data, describe how a screen should be guarded against parties at a distance, and specify appropriate workstation use. (Mandatory)
- Protect mobile – You want a mobile device policy that removes data before a device is circulated to another user. (Mandatory)
- Track servers – You want all your infrastructure in an inventory, along with information pertaining to where it’s located. Copy all data completely before you move servers. (Recommended)
What administrative safeguards are needed?
- Risk Assessment – Identify, analyze, create then put measures in place to resolve the actions by completing a comprehensive risk assessment for all health data. (Mandatory)
- Systematic risk management – risk assessment is an ongoing process that must be reassessed at regular intervals with measures put in place to reduce the risks to an appropriate level. A sanctions policy must be introduced for employees who fail to comply with HIPAA regulations. (Mandatory)
- Train your staff – You need to train employees on all ePHI access protocols and how to recognize potential cybersecurity risks such as phishing, hacking, and deception. A record of these sessions must be kept. (Recommended)
- Build contingencies – You must be able to achieve ongoing business continuity, responding to disasters with a preparation process that keeps data safe. (Mandatory)
- Test your contingencies – You must test your contingency plan on a regular basis, with relation to all key software. A backup system and restoration policy should be adopted. (Recommended)
- Block unauthorized access – Be certain that parties that haven’t been granted access, such as subcontractors or parent companies, cannot view ePHI. Sign business associate agreements with all partners. (Mandatory)
- Document all security incidents – Note that this step is separate from the Breach Notification Rule, which has to do with actual successful hacks. A security incident can be stopped internally before data is breached. Staff should recognize and report these occurrences. (Recommended)
HIPAA Privacy Rule
HIPAA’s Privacy Rule is in place to ensure that Patient Health Information (PHI) is protected. The Privacy Rule is actually called “Standards for Privacy of Individually Identifiable Health Information.”
- Respond promptly – HIPAA legislation gives you just 30 days to get back to patient access requests. (Mandatory)
- Notice of Privacy Practices – An NPP is required to officially inform patients and subscribers of data-sharing policies. (Mandatory)
- Privacy Training – Beyond the training described above, make sure your personnel understands what data can and cannot be shared internally and externally (Required)
- Do not succumb to corruption – “Ensure appropriate steps are taken to maintain the integrity of ePHI and the individual personal identifiers of patients,” instructs HIPAA Journal. (Mandatory)
- Get authority – get permission from the patient to use redacted ePHI for research, fundraising, or marketing. (Mandatory)
- Update your copy – Your authorization forms should now include a reference to changes in the treatment of school immunizations, ePHI restriction in disclosure to health plans, and the right of patients to their electronic records. (Mandatory)
HIPAA Breach Notification Rule
HIPAA’s Breach Notification rule sets out requirements for who to notify in the event of a protected health data breach.
- Know the notification process – If a breach of ePHI occurs, you have to make both your patients and the HHS Department aware. If more than 500 people’s records are involved, you also must notify the media. (Sound like fun?) If it’s under 500 patients you have to submit a small-scale hack form through the OCR website. “These smaller breach reports should ideally be made once the initial investigation has been conducted,” said HIPAA Journal. “The OCR only requires these reports to be made annually.” All of the immediate notifications must be completed within 60 days after discovery. (Mandatory)
- Check twice for four – Make sure that your breach notification message contains these four elements:
- A description of the ePHI and personal identifiers involved in the breach
- Who gained unauthorized access to PHI or related information
- Whether details were simply seen or taken – viewing vs. acquirement (if you know)
- The degree to which risk mitigation has succeeded. (Mandatory)
HIPAA Final Omnibus Rule
The HIPAA Omnibus rule sets out additional requirements for covered entities and business associates affected by HIPAA.
- Refresh your BAA – Update your Business Associate Agreements to reflect the changes of the Omnibus Rule. (Mandatory)
- Send new BAA copies – get signed copies of the new BAA (with the Omnibus information incorporated) to stay compliant. (Mandatory)
- Refresh your privacy policy – Privacy policies must also reflect Omnibus changes. (Mandatory)
- Update the Notice of Privacy Practices – “NPPs must be updated to cover the types of information that require authorization, the right to opt-out of correspondence for fundraising purposes and must factor in the new breach notification requirements,” advised HIPAA Journal. (Mandatory)
- Finalize your training – Make sure that everyone on your staff is aware of all Omnibus Rule adjustments by conducting thorough training. (Recommended)
HIPAA Compliance Guide
In part 2 of this article, we will dig deeper into the world of HIPAA compliance. To become HIPAA compliant, any healthcare organization should aim to achieve all of the mandatory and recommended actions in part 1.
If an item is recommended or addressable, it does not mean it is optional. Take encryption, for example; on paper, it is a recommended action, but if the healthcare organization does not use encryption, they must provide a roadmap of how they intend to introduce encryption.
What are the Five Main Directives of HIPAA?
HIPAA’s five main parts include:
- HIPAA Title I focuses on the often forgotten insurance reform that was introduced in HIPAA, introducing rules about the access, portability, and renewability of health insurance. Making it possible to maintain coverage when your employment changes and making it unlawful for group insurance plans to turn down health cover.
- HIPAA Title II concentrates on the mandatory steps of the Privacy Rule, Security Rule, and Enforcement Rule. It also establishes the national standards of how electronic healthcare transactions are processed as set out by the U.S. Department of Health and Human Services (HHS)
- HIPAA Title III introduces new tax rules related to healthcare treatment including the provisioning of certain deductions for medical insurance.
- HIPAA Title IV includes additional details on the reform of insurance law, with protections for those who have pre-existing conditions and individuals who want to maintain their insurance.
- HIPAA Title V gives guidelines for life insurance policies that are owned by businesses and how to handle income tax specifics when someone has their US citizenship revoked.
As an experienced HIPAA-compliant IT service provider, one that is responsible for processing, transferring, and storing health data on behalf of our customers, the majority of our dealings are with HIPAA Title II. This part of the law is known as the Administrative Simplification Provisions.
It establishes and describes these five elements:
- National Provider Identifier Standard – 10-digit NPI (national provider identifier) numbers must be assigned to all healthcare entities.
- Transactions and Code Set Privacy Standard – this objectively approved protocol must be used in electronic data interchange (EDI).
- HIPAA Privacy Rule – Ensuring that Patient Health Information (PHI) is protected. The Privacy Rule is actually short-hand for the “Standards for Privacy of Individually Identifiable Health Information.”
- HIPAA Security Rule – This rule delineates expectations for the safeguarding of patient data. The Security Rule is short-hand for the “Security Standards for the Protection of Electronic Protected Health Information.”
- HIPAA Enforcement Rule – This subsection of the law provides parameters with which companies should be investigated for potential or alleged violations.
HIPAA Compliance Terms You Need to Know in 2024
Probably the three most important HIPAA Compliance terms you need to know in 2024 are:
- Protected Health Information (PHI)
- Covered Entity (CE)
- Business Associate (BA)
Protected Health Information
Protected health information (PHI) is any patient data that the law is meant to safeguard, data that can be used to identify an individual. Common examples include names, email addresses, social security numbers, insurance certificates, and so on.
Covered Entity
A covered entity (CE) is any healthcare provider, health plan, or health data clearinghouse. This commonly includes doctors, clinics, pharmacies, etc.
Business Associate
A business associate is any 3rd party organization that handles individually identifiable health data on behalf of a covered entity.
What is the Primary Purpose of HIPAA Regulations?
The main objective of HIPAA regulations is to uphold and protect the data integrity of Protected Health Information (PHI). Of key concern to covered entities and businesses, associates are the Privacy Rule, Security Rule, and Breach Notification Rule.
- The Privacy Rule creates standards for the privacy of PHI.
- The Security Rule standardizes the handling of electronically protected health information (ePHI)
- The Breach Notification Rule mandates that covered entities and business associates must alert any affected parties whenever their protected health information is compromised.
HIPAA Compliance for Covered Entities Versus Business Associates
One of the most important elements of HIPAA compliance is defining who is responsible for each HIPAA parameter. Previously, a responsibility matrix was created to define distinctions between all parties. However, since the HIPAA Final Omnibus Rule, business associates are now directly responsible for meeting all HIPAA requirements.
Covered Entity
Nonetheless, by definition, a HIPAA-covered entity is a healthcare plan, healthcare provider, or healthcare data clearinghouse that electronically sends and/or receives protected health information (PHI) as described by HIPAA and HHS standards. The transmission of PHI – or ePHI (electronic PHI) – often occurs for one of two reasons: healthcare-related financial transactions or insurance processing.
Business Associate
A HIPAA business associate is a person or organization that is not employed by a healthcare plan, provider, or clearinghouse, but that completes tasks related to individually identifiable health information, as governed by the HIPAA Administrative Simplification Rules (which include the all-important Privacy Rule and Security Rule).
Atlantic.Net is a business associate, as we provide a HIPAA-compliant hosting service that handles ePHI on behalf of our clients.
What Privacy Rights Exist for Health Data?
The Privacy Rule gives patients the right to receive a notice of privacy practices (NPP), a document that defines how healthcare providers protect patient privacy. The NPP focuses on individual privacy issues and concerns, prompting users to open discussions with health plans and health care providers to exercise their privacy rights.
Also according to the Privacy Rule, healthcare providers and plans have to be responsive when their patients ask for the following:
- Access to their health records
- Changes to be made to their PHI (in the case of errors)
- Records of disclosure
- Doctor-patient communications
Limitations to apply to data use and disclosure.
What did the HIPAA Omnibus Rule introduce?
A major change to the HIPAA compliance rules came in January 2013, when the HHS announced its Omnibus Rule for HIPAA. This rule required that healthcare providers meet certain additional security requirements by September 23, 2013.
The maximum fine for a single violation was significantly raised to $1.5 million. HHS Secretary Kathleen Sebelius described the new rule in the agency’s official announcement. “Much has changed in health care since HIPAA was enacted over fifteen years ago,” she said. “The new rule will help protect patient privacy and safeguard patients’ health information in an ever-expanding digital age.”
Bear in mind that the specifics of the rule are beyond the scope of this article, but are built into the tips and checklist for compliance below.
What Happens If I Violate HIPAA Regulations?
Based on the Breach Notification Rule, healthcare providers and plans must report any possible exposure of protected health information whenever data is stolen, lost, or otherwise compromised. If the exposure includes more than 500 people, the HIPAA CE must also quickly contact the HHS Secretary. Local media must be notified in a state or jurisdiction in which 500 or more affected individuals reside. If fewer than 500 people are impacted, the individuals must be alerted, and the HHS Secretary must be sent a report within 60 days following the end of the calendar year.
Covered entities and business associates sometimes fail to comply with HIPAA. These violations are discovered through random audits, investigations, breach notifications, other governmental agencies, and the press.
There are four levels of violations described by the HIPAA Enforcement Rule (with minimum fine per incident in parentheses):
| The entity was unaware and would have remained unaware based on reasonable measures | $100 to $50,000 |
| “Reasonable cause” – in which the violation was caused by an element that would prompt action in an ordinary person | $1000 to $50,000 |
| “Willful neglect” – in which the violation was caused by intentional avoidance but rectified within 30 days | $10,000 to $50,000 |
| Willful neglect but not mitigated within 30 days | $50,000 |
What Does HITECH Have to Do With Healthcare?
HITECH is the acronym behind the Health Information Technology for Economic and Clinical Health Act of 2009. The legislation, signed into law by President Obama on February 17, was intended to accelerate the transition to electronic health records (EHR). It was actually included within the American Recovery and Reinvestment Act of 2009 (ARRA), which was geared toward stimulating the economy.
Another result of HITECH has to do with the Office of the National Coordinator for Health Information Technology (ONC), which has been part of the HHS Department since 2004. The ONC became responsible for the administration and creation of standards related to HITECH.
The HITECH law is geared more toward the adoption of electronic health records rather than toward specific security rules for digital data. Many HIPAA hosting providers and similar entities are certified for compliance with both HITECH and HIPAA to demonstrate their knowledge of (and adherence to) all federal healthcare law.
As you can imagine, there is an overlap between HIPAA and HITECH laws. However, HITECH serves as something of an addendum to HIPAA. It mandates that any standards for technology arising from HITECH must meet the HIPAA Privacy and Security Rules.
Top Tips for HIPAA Compliance
By now you will probably understand that HIPAA is not a simple law to comply with. In part 3 of this article, we will provide our Top Tips for achieving HIPAA compliance.
Let’s first look at the legacy advice drawn up during the early years of HIPAA which is still completely relevant today; then, in the next section, we will get into some of the more recent rule changes. Finally, we’ll provide a checklist that incorporates this advice into actionable steps so you can manage compliance simply and effectively.
Expert Security Tips for HIPAA Compliance
HIPAA expert Raj Chaudhary, who leads the security and privacy teams at consultancy group Crowe Horwath, suggested these tips. While this list was compiled prior to the Final Omnibus Rule of 2013, the tips are still vitally important:
- Keep data in the appropriate hands by strengthening security with logins. Ensure that only the people that need access to ePHI have a user ID or a user account, and policies are in place to change default passwords and increase password complexity.
- Monitor controls and makes sure logging is working correctly. A key aspect of complying with the HIPAA Security Rule is that you pay close attention to access to PHI. Simply put, you want to log everything. IT personnel should make sure that the logging feature is active within all systems around the clock. In addition to logging, you want to directly monitor via a system of rules, so you can examine your data accumulation process and be certain that everything is continually meeting your access controls.
- Assess your access controls at all layers, including the network and your software. At the level of the network, you should have user IDs and strong passwords. This level of security is usually less problematic because it’s managed directly by IT. The other critical layer, though, is the software. You need to maintain control of that layer. Plus, although it’s annoying to users to get locked out of their accounts, Chaudhary noted that it’s a lesser evil to get hacked. “[A]s an example, if somebody externally breaks in through your firewall to get to your systems and is now trying to guess the password, you’ve got to make sure that you have some sort of a lock-out after a few of these attempts,” he said. “I typically recommend that after 10 failed attempts, one should be locked out.”
- Pay careful attention to your business associates who are handling any PHI, aka protected health information. Chaudhury recommended carefully reviewing your business associate agreement (BAA) that controls your data relationship with each vendor that is handling your data. Since the introduction of the Final Omnibus Rule, business associates are directly responsible for meeting the parameters of HIPAA compliance –in other words, you are now less exposed by the law since the vendors carry some of the burdens. Nonetheless, due diligence is still necessary.
The Four-Step Plan
There is no one-size-fits-all set of requirements for HIPAA legislation. However, the idea of the four-step plan is that it gives healthcare organizations and associates a great starting place to become compliant.
- Carefully read and sign a business associate agreement with the vendor.
- Make sure you are in compliance with the “minimum necessary” protection. To be clear, “minimum necessary” means that you only disclose the amount of information that you absolutely have to. It’s an expectation set forth in the HIPAA Privacy Rule.
- Conduct a performance assessment of the vendor.
- Every year, reassess whether or not the business associate is in compliance with the BAA.
According to Chaudhary, covered entities often do not keep ongoing or updated records on a BAA. “The agreements are not all consistent and not updated on a regular basis,” he said. “And most likely, people don’t apply the ‘minimum necessary’ rule and they provide more information than is necessary to perform that series of tasks that they were hired to do.”
Create an All-Encompassing, Step-by-Step Procedure for Incident Response and Business Continuity.
Business continuity planning must be robust, and incident response planning needs to be fully described within your final documents. To manage business continuity, it is essential to conduct a business impact assessment, leading to a business continuity plan, and finishing out with a disaster recovery plan.
When you are putting together the business impact assessment, keep in mind that your goal is to have a reasonably good gauge of mission-critical systems – telling you the recovery time objectives that must be met in order to keep any expenses arising from a loss of business continuity to a minimum.
Three Specific HIPAA Compliance Tips You Need to Know Post-Omnibus
The Office for Civil Rights (OCR) of the HHS Department started performing HIPAA compliance audits more aggressively in 2016. Businesses are understandably concerned about audits because they don’t want to end up in a publicity nightmare, with their competence and credibility called into question.
Prior to 2016, audits only occurred following a complaint or news report on problematic activity at a particular covered entity or business associate. A 2015 report found that the OCR was not doing enough to manage HIPAA compliance.
In 2016, the OCR “strengthen[ed] its review efforts by implementing the second phase of audits that were scheduled to occur in 2014, but encountered a number of delays,” noted Clyde Bennett in Help Net Security. For the assessments that took place in 2016, “providers with fewer than 15 physicians and healthcare business associates will be subject to audits,” he added.
It’s important to update your procedures and related documents so that you are up-to-date with HIPAA compliance following the adjustments made within the Final Omnibus Rule. Here are three basic considerations:
- BAA 2.0 – You want your business associate agreement to reflect the Omnibus Rule, which broadened responsibility for HIPAA compliance to include business associates. It is now legally necessary for business associates to directly follow all HIPAA laws.
- Next-gen privacy policy – Another big part of the Omnibus Rule was revisions of privacy parameters. Changes were made in the treatment of deceased patients, patient access rights, response to ePHI requests, disclosure to insurance and Medicare, data distribution, immunizations, and how to handle data for marketing, fundraising, and research purposes.
- Forward-focused training – Your staff needs to know how this critical healthcare law is changing, as indicated by the Omnibus Rule. Provide training to keep your business free of fines and lawsuits. Business associates need to train as well. Document this effort so you’re audit-ready.
See Additional Guides on Key Compliance Management Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of compliance management.
HIPAA compliant hosting
- How to Make a HIPAA-Compliant Website in 2024
- HIPAA Compliant Server for a Client Portal Solution
- Best Practice for Creating a HIPAA-Compliant WordPress Site
PCI compliant hosting
- What is PCI Compliance in 2024?
- PCI DSS Cybersecurity Requirements: A Practical Guide
- Small Business PCI Compliance Guide
HIPAA IT compliance
- HIPPA or HIPAA? HIPAA vs. HIPPA – What’s the Difference?
- Best HIPAA-Compliant Fax Services in 2024
- Best HIPAA-Compliant Email Service in 2024
HIPAA Compliant Hosting
Are you in need of an infrastructure that can protect the health data of your organization? At Atlantic.Net, whatever your technical requirements, we can offer a top-grade HIPAA-Compliant Web Hosting solution. Get a HIPAA-Compliant Server Cost from one of our experts.
Get a free consultation today!
HIPAA Compliance Checklist PDF
Click here to download the HIPAA Compliance Beginner’s Guide PDF
Read More About HIPAA Compliance
- How to Become HIPAA Compliant
- What Is the HIPAA Security Rule?
- Top Considerations for HIPAA File Storage
- HIPAA Data Storage Requirements
- Protecting e-PHI in the Cloud
- What Is HIPAA Cloud Computing?
- What Is Healthcare Hosting?
- What Is PHI?
This article was updated with the latest information on January 9, 2024.
Get a $250 Credit and Access to Our Free Tier!
Free Tier includes:
G3.2GB Cloud VPS a Free to Use for One Year
50 GB of Block Storage Free to Use for One Year
50 GB of Snapshots Free to Use for One Year